Real-Time Behavioral Analysis for Modern Malware
Are our old ways of staying safe online keeps up with new threats? Malware is getting smarter, and our old methods aren’t enough to protect us anymore.
We’re seeing a big change in how we fight cyber threats. New tools like Phantom Software, CrowdStrike, and Sentinel One are leading the way. They use AI-powered behavioural analysis to spot and stop threats fast.
In this new world, real-time behavioural monitoring is key to fighting malware. By watching how files and network traffic act, we can catch threats early.
Key Points:
- Modern malware is becoming increasingly sophisticated, rendering traditional detection methods ineffective.
- Real-time behavioural analysis is crucial for detecting and responding to cyber threats.
- AI-powered solutions are driving the shift towards proactive cybersecurity measures.
- Organisations must adopt a proactive approach to cybersecurity to stay ahead of emerging threats.
- Effective modern malware defence relies on the ability to analyse behaviour in real-time.
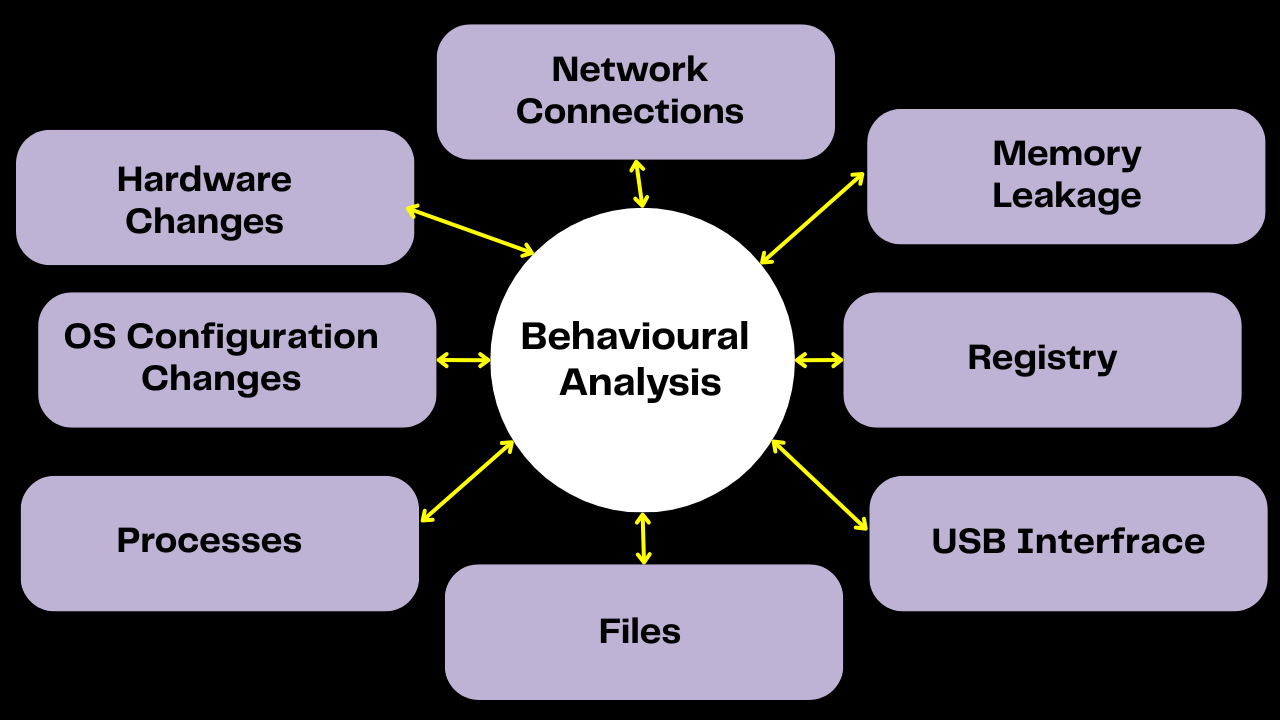
The Evolving Threat of Modern Malware
In the world of cybersecurity, modern malware poses a big threat. We need to be proactive and keep our defences up to date. It’s key to understand how malware has changed and what it means for our security.
How Malware Has Evolved in Recent Years
Malware has become much more complex and sneaky. Attackers use tricks like hiding in plain sight and changing its form. For example, Phantom Software can look like normal software, making it hard to spot.
Why Traditional Detection Methods Fall Short
Old ways of catching malware, like looking for known patterns, don’t work anymore. Modern malware changes too fast for these methods. CrowdStrike shows that we need new, behaviour-based ways to detect threats.
The Growing Need for Proactive Security Measures
We need to be proactive to keep up with malware. Organisations should use real-time monitoring to catch threats early. This way, we can stay safe from the latest malware threats.
“The key to effective cybersecurity lies in understanding the evolving threat landscape and adopting proactive measures to counter it.”
By knowing how malware has evolved and the flaws in old detection methods, we can improve our security. This will help protect our organisations from the dangers of modern malware.
Real-Time Behavioral Monitoring: The Foundation of Modern Defense
The world of malware is changing fast. We must now focus on real-time behavioral monitoring as a key part of our defense. Old ways of detecting threats are not enough anymore. We need to act quickly to stop threats before they can harm us.
Defining Behavioural Analysis in Cybersecurity
Behavioural analysis in cybersecurity watches how systems and users act. It looks for patterns that might show something bad is happening. This way, we can spot threats that traditional methods might miss.
Comparing Signature-Based vs. Behaviour-Based Detection
Signature-based detection uses a list of known threats to find malware. But it can’t catch new threats. Behaviour-based detection watches for odd behaviour, whether it’s new or known. This makes it a better defence against today’s malware.
Core Components of an Effective Monitoring System
An effective monitoring system needs a few important parts:
- Real-time analytics: This lets us quickly check data as it comes in, helping us act fast against threats.
- Machine learning algorithms: These find patterns and oddities that might mean trouble.
- Comprehensive visibility: The system should show us everything happening on the network and systems.
With these parts, organisations can build a strong defense against modern malware.
How Behavioural Analysis Identifies Malicious Activity
Cyber threats are getting smarter, and so are we. Behavioural analysis is a key tool in spotting bad activity. It looks at how malware acts, not just what it is. This makes it better at catching and stopping threats.
Key Malware Behavioural Indicators
Malware shows certain signs that it’s up to no good. These behavioural indicators include:
- Unusual network activity, like unexpected connections.
- Abnormal system changes, like changes to system files or registry entries.
- Suspicious user activity, like login attempts from unknown places.
The Role of Machine Learning Algorithms
Machine learning algorithms are vital in behavioural analysis. They look at patterns and oddities in system and user behaviour. This helps spot threats that old methods might miss. Our machine learning gets better over time, thanks to experience.
Heuristic Analysis Techniques
Heuristic analysis checks if files and programs act like malware, even if they’re not known. This way, we can find new and unknown threats. Key techniques include:
- Watching system calls for signs of trouble.
- Looking at code execution patterns for oddities.
- Testing software in a safe environment.
By using behavioural indicators, machine learning, and heuristic analysis, we can better fight malicious activity.
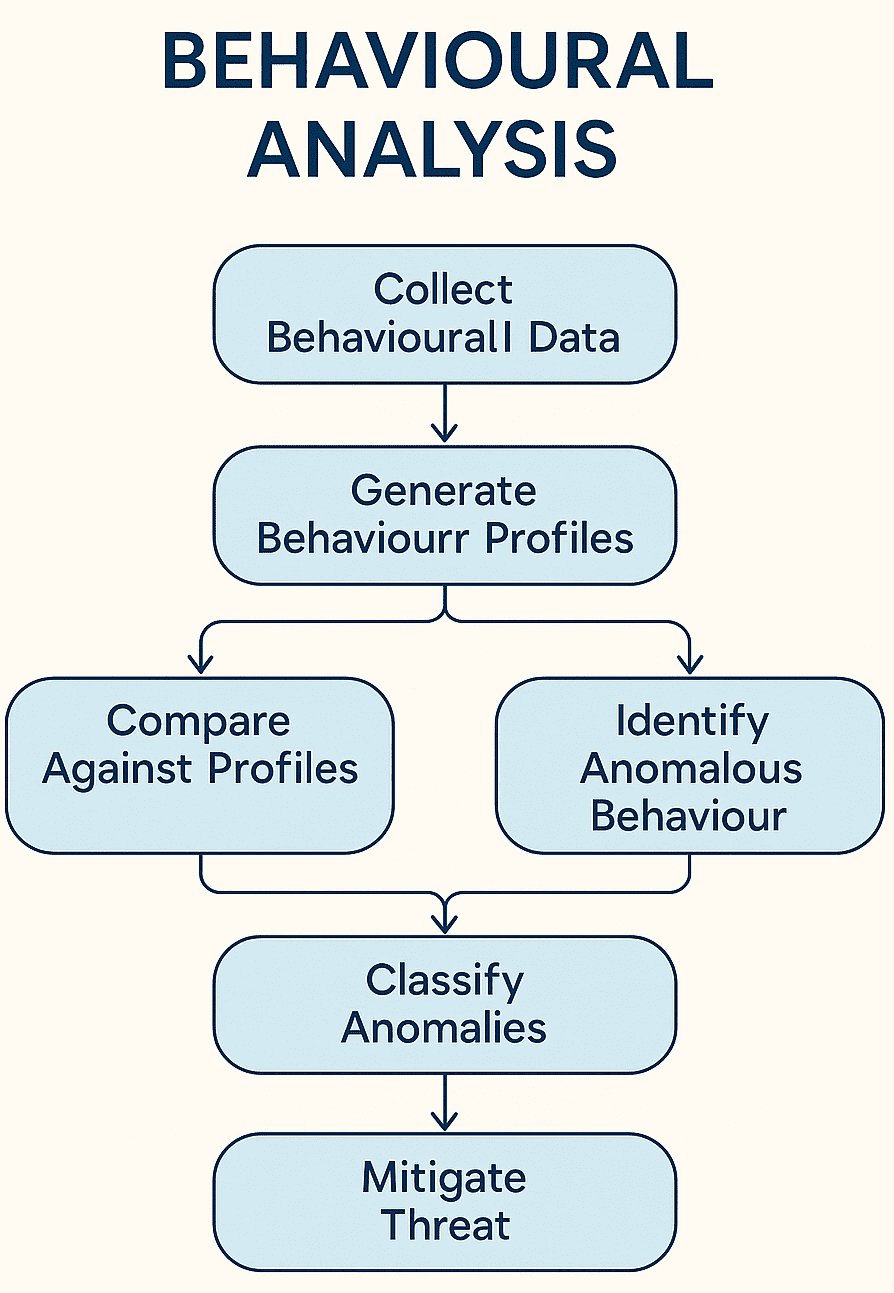
Essential Tools for Implementing Real-Time Monitoring
The success of real-time monitoring depends on the tools used for behavioural analysis. As threats get more complex, the need for strong behavioural analysis solutions grows.
Commercial Behavioural Analysis Solutions
Companies like SentinelOne and CrowdStrike offer top-notch AI-powered tools. These tools spot and act on threats fast, using machine learning to catch bad activity.
Open-Source Monitoring Tools
Open source monitoring tools are great for those on a tight budget or needing custom features. They’re flexible and get better thanks to community help, but need some tech know-how to set up.
Integrated Security Platforms with Behavioural Capabilities
Today’s security platforms often include behavioural analysis. They help protect better and can be divided into:
- Enterprise-Grade Solutions: Made for big companies, these have advanced features and grow with your business.
- SMB-Friendly Options: For smaller businesses, these offer key behavioural analysis tools at a lower price.
Choosing the right tool is key. Think about your business size and security needs. The right monitoring tools and behavioural analysis solutions boost your real-time monitoring.
Setting Up Your Behavioural Monitoring Infrastructure
A strong cybersecurity posture starts with a good behavioural monitoring system. As cyber threats get more complex, a solid monitoring setup is key.
Hardware and Network Requirements
First, check your hardware and network needs for monitoring. Make sure the system can handle lots of data. Also, think about network bandwidth and segmentation to avoid bottlenecks.
Important things to consider are:
- Scalability for growing data
- Redundancy for continuous operation
- Fast data processing
Deployment Architecture Best Practices
Follow best practices for deploying your monitoring system. Use a distributed architecture for better scalability and resilience. Also, monitor both networks and endpoints for full visibility. Make sure it works well with other security tools and incident response.
Good deployment also means:
- Doing network assessments to find the best monitoring spots
- Setting up data retention policies
- Following data protection laws
Integration Points with Existing Security Systems
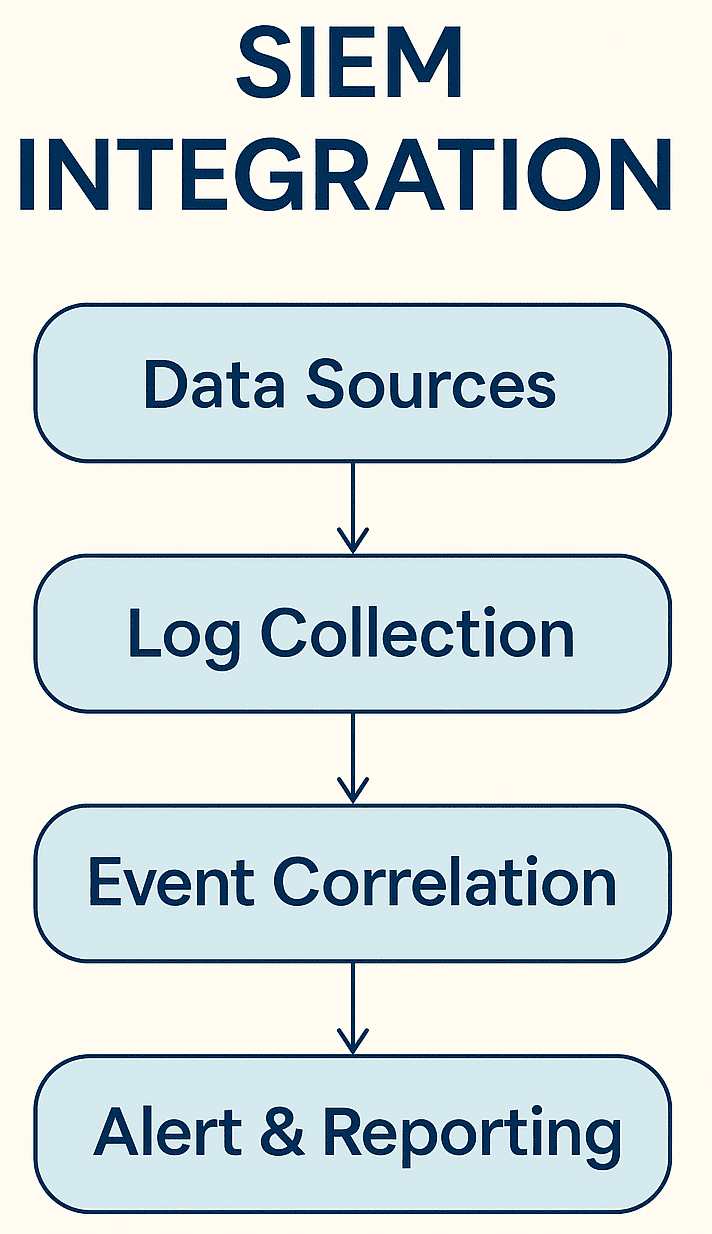
It’s important to link your monitoring system with other security tools. Focus on SIEM systems and endpoint protection.
SIEM Integration
Linking with SIEM systems helps combine behavioural data with other security events. This makes your security stronger and better at detecting threats.
Endpoint Protection Coordination
Working with endpoint protection lets you act fast on threats. This means isolating infected devices or applying patches quickly, reducing damage.
With a well-planned monitoring setup, you can boost your cybersecurity. This helps defend against new threats proactively.
Configuring Effective User Activity Tracking
Tracking user activity is key to spotting security threats quickly. It helps organisations see when something unusual happens. We’ll look at how to set up tracking, including creating normal behaviour profiles and following data protection rules.
Establishing Normal Behaviour Baselines
Creating normal behaviour profiles is the first step to spotting threats. Behavioural analysis makes a map of usual user actions. This includes when they log in, where they are, and what data they access. Knowing what’s normal helps spot when something is off.
Setting Up Website Visitor Tracking Parameters
It’s important to track how visitors use your website. This means setting up tools to watch page visits and how users click. Website visitor tracking helps understand user habits, find security risks, and make websites better for users.
Implementing Online Behaviour Monitoring
Online behaviour monitoring uses special tools to watch user actions live. It looks for things like odd login attempts or unusual data sharing. Machine learning algorithms and rules help spot and deal with threats better.
Privacy Considerations and GDPR Compliance
When tracking user activity, privacy is a big deal. You must follow rules like the GDPR. It’s about keeping security strong while protecting user privacy. This means being open about data use, getting the right permissions, and using strong privacy measures.
By setting up good user tracking and following privacy laws, companies can improve their security. They also make sure they respect users’ rights.
Developing Real-Time Analytics Capabilities
Improving our cybersecurity is key, and real-time analytics play a big role. CrowdStrike and SentinelOne show how AI changes the game. It makes threat detection more accurate and quicker.
Creating Custom Detection Rules
We must make custom detection rules for our security needs. This means knowing our systems’ normal behaviour and spotting signs of trouble. These rules help us catch threats fast.
Machine learning helps us watch user behaviour for signs of danger. This way, we can stop threats before they start. It keeps us safe from security breaches.
Configuring Alert Thresholds and Priorities
Setting up alert thresholds and priorities is vital. It helps our system give us useful info without flooding us with false alarms. By setting the right levels, we focus on the biggest threats.
- Set clear rules for what alerts are most important
- Use past data and threat info to set alert levels
- Keep checking and tweaking alert settings to get better at spotting threats
Implementing Automated Response Actions
Automated responses are key to a strong real-time analytics system. They help us act fast when security issues arise. This reduces the harm caused by threats.
When setting up automated responses, consider these points:
- Have clear plans for how to handle different security issues
- Make sure automated tools work well with our security setup
- Keep an eye on and update automated actions to keep them effective
By focusing on real-time analytics, we boost our cybersecurity. This includes making custom rules, setting up alert levels, and using automated responses. It helps us stay one step ahead of threats.
Responding to Behavioural Alerts Effectively
When a behavioural alert is triggered, our response is key. It can greatly affect the outcome of a security breach. Quick and effective incident response is vital to reduce the breach’s impact and get things back to normal fast.
Building a Structured Incident Response Plan
A solid incident response plan is essential for good cybersecurity. It shows how to act in a security incident, ensuring a fast and organised response. SentinelOne says defining roles and responsibilities is crucial. It helps avoid confusion and overlapping efforts during an incident.
Triage and Prioritisation Strategies
Triage and prioritisation are key to handling behavioural alerts well. By sorting alerts by severity and impact, we use our resources better. CrowdStrike recommends a tiered alert system. It helps tell apart low-risk and high-risk threats, making the response smoother.
Containment and Remediation Techniques
Containment and remediation are crucial in dealing with behavioural alerts. The aim is to lock down affected systems and remove the threat before it can spread.
System Isolation Procedures
System isolation means cutting off affected systems from the network to stop further harm. This can be done through network segmentation or physically disconnecting devices, as experts agree.
“Isolation is a critical step in preventing the lateral movement of malware.”
Malware Removal Best Practices
Removing malware effectively needs a deep understanding of its behaviour and impact. Best practices include using special tools to remove malware and restoring systems from clean backups. It’s also key to update security measures to avoid re-infection.
By taking a structured approach to handling behavioural alerts, organisations can boost their cybersecurity. This means having the right tech, clear processes, and trained staff.
Troubleshooting Common Challenges in Behavioural Monitoring
Behavioural monitoring has many benefits, but also faces challenges. These challenges are key to keeping our security strong. It’s important to understand them well.
Addressing False Positive Issues
False positives can really slow down behavioural monitoring. Fine-tuning detection rules and regularly updating what’s normal can help. This makes the system more accurate.
Having a feedback loop for security teams to report false positives is also helpful. It helps improve the system’s accuracy over time.
Optimising System Performance
Behavioural monitoring can use a lot of resources. This can slow down systems. Optimising the monitoring infrastructure is key. It’s important to make sure it fits the organisation’s size and complexity.
Checking and adjusting the system regularly keeps it running smoothly. This is crucial for its performance.
Handling Evasive Malware Techniques
Evasive malware is a big challenge for behavioural monitoring. Advanced machine learning algorithms and behavioural analysis techniques can help. They help detect and respond to threats.
Keeping up with the latest threat intelligence is essential. It helps fight against new evasive techniques.
Scaling Solutions for Growing Organisations
As organisations grow, their monitoring solutions need to grow too. Cloud-based solutions are flexible and scalable. They’re perfect for growing companies.
It’s important to regularly check if the monitoring can handle more data and traffic. This ensures it stays effective.
Conclusion: Staying Ahead in the Malware Arms Race
Modern malware keeps changing, and old ways of detecting it are not enough. We need to be proactive in defending against malware. This means using real-time behavioral analysis to keep up with new threats.
CrowdStrike’s AI-Powered Behavioral Analysis in Cybersecurity shows us the way forward. It uses advanced technology to fight off complex malware. This helps us strengthen our defences and deal with threats quickly.
Our research highlights the value of real-time monitoring and machine learning. These tools help spot and stop malicious activities. By keeping up with these strategies, we can keep our systems safe and stay alert to new dangers.
To stay ahead in the fight against malware, we must keep innovating and be proactive in cybersecurity. By focusing on real-time analysis and using the latest defence tools, we can protect our digital world. This will help us build a safer future.







