How to Protect Website Form with Proper Input Validation
Back in 2016, when I was new to cybersecurity, I went to a security conference to learn more about the field. There, I met a white-hat hacker who casually said, “I’ve hacked thousands of websites just by using their web forms.”
I didn’t believe him at first, so I asked him to try one of my custom PHP forms. To my surprise, he cracked it in just a few minutes. I was shocked.
We later sat down for a coffee, and he explained the importance of input validation, how websites need to check what users enter in their forms. Since that day, I’ve seen many websites get hacked just because they didn’t handle form input properly.
Introduction
Imagine your website is your awesome online clubhouse. People come to visit, fill out forms to join your mailing list, place orders for your cool stuff, or leave you amazing comments. These forms are like the front doors and windows of your clubhouse. They’re how information gets in.
Now, what if those doors and windows weren’t very strong? What if anyone could just slip in whatever they wanted, or even try to break things from the inside? That’s where input validation comes in! It’s like having a super-friendly but very strict bouncer at your website’s front door, making sure only the right kind of information gets in, and keeping the troublemakers out.
What Are Web Forms, and Why Do They Matter?
Consider web forms to be the welcoming front desk of your website. They welcome guests and gather vital data, such as names, email addresses, and comments. Web forms, whether they are a straightforward login box or an intricate checkout form, help users connect with your website.
Your website could feel like a locked door without these forms – no engagement, no entry. Web forms are helpful, but if they are not used carefully, they can also be a double-edged sword.
What Is Input Validation?
Input validation is the process of checking the data that users submit through your forms. Think of it as a security guard that verifies IDs at a gate.
Here’s what input validation does:
- Ensures only the right kind of information is accepted (like names instead of numbers).
- Rejects unexpected or harmful data.
- Protects your website from abuse, spam, and attacks.
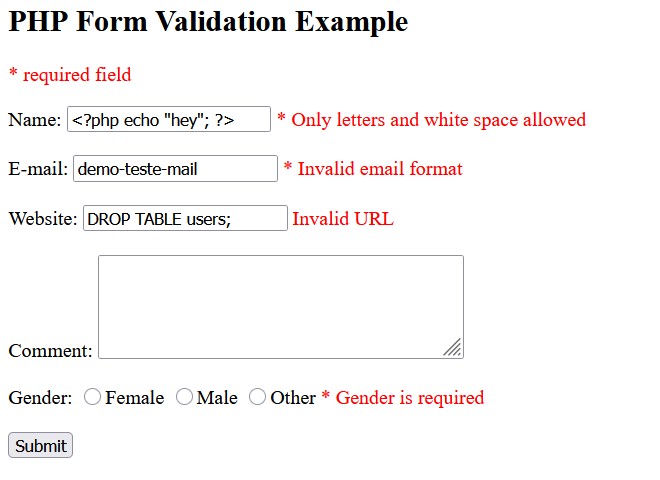
Example: If someone enters “DROP TABLE users;” into your contact form instead of a name, input validation will reject it. Without validation, that little line of code could delete your user database. Scary, right?
Input Validation: The Hero
So, what’s this “input validation” we keep talking about?
Input validation is the process of checking the information that users submit through web forms before it’s processed by the website’s server or stored in its database. It’s like the bouncer checking IDs and making sure people aren’t carrying anything they shouldn’t be.
There are two types of input validation:
Client-Side Validation: This is the first line of defense. It happens in the user’s browser before the data is sent to your server. Think of it as catching errors before they even leave home.
Server-Side Validation: This is the second layer of security. It checks the data on your server to ensure nothing harmful sneaks through. After all, client-side validation can be bypassed by clever hackers.
How does input validation work?
Here’s how it works:
- User Input: You, the visitor, fill out a field in a web form (like your email address).
- Validation Rules: The website has rules set up for that field (like “it must look like an email address”).
- The Check: The website’s code (or sometimes your browser) checks if what you typed follows those rules.
- Feedback:
If it’s okay: Your information is accepted and processed.
If it’s not okay: The website will usually tell you what went wrong (like “Please enter a valid email address”).
Why Bother Being So Picky About What People Type? [Why Input Validation Matters]
You might be thinking, “Why can’t we just trust people to type the right stuff?” Well, unfortunately, not everyone has good intentions, and even well-meaning folks can make mistakes!
Without input validation, hackers can do all kinds of nasty stuff like:
- Inject malicious code (SQL Injection, XSS)
- Access sensitive user data
- Break your site layout
- Submit fake entries or spam
- Take control of your backend
Letting users send unchecked data is like letting a stranger walk straight into your server room without asking who they are.
Real-Life Horror Stories: When Bad Validation Leads to Big Trouble
Sadly, these aren’t just theoretical problems. Lack of proper input validation has caused major security breaches in the real world. Let’s take a look at these incidents that highlight just how serious poor input validation can be:
- GreenShift Plugin Vulnerability (April 2025)
Over 50,000 WordPress sites were at risk due to an input validation flaw in the GreenShift plugin. Hackers exploited a file upload feature that didn’t properly check the uploaded files. This let them upload PHP backdoors, giving full access to the website. - MOVEit Transfer Data Breach (2023)
Though not WordPress-specific, the MOVEit Transfer platform suffered a critical breach due to an input handling vulnerability. Hackers were able to steal data from several government and corporate systems. The root cause? Lack of input sanitation allowed attackers to inject malicious commands. - Progress LoadMaster Breach (CVE-2024-56131)
An input validation flaw allowed users to execute OS command injection attacks, exposing sensitive data and compromising entire systems. - Microsoft Outlook Vulnerability (CVE-2024-21413)
Improper input validation let attackers exploit hyperlinks in emails. This led to remote code execution, putting users’ systems at risk.
How to Implement Input Validation (The Smart Way)
So, how do you become a super bouncer for your website forms? Here are some key ways to implement input validation:
1. Set Clear Rules
- Only accept the type of data you need:
- Emails must be valid addresses
- Names should only contain letters
- Numbers should be in a proper range
- Files should only be accepted if they’re the correct type (like .jpg, not .php)
2. Use Both Client-Side and Server-Side Validation
- Client-side validation happens in the browser (using JavaScript) — quick, but not secure on its own.
Using HTML5: Modern HTML provides built-in attributes for basic validation, like required, type=”email”, minlength, maxlength, and pattern (for custom rules using regular expressions). These are easy to implement and provide immediate feedback to the user.JavaScript: For more complex validation rules or custom error messages, you can use JavaScript. You can write code to check if a password meets certain criteria, if two email fields match, or if a selected date is in the future. - Server-side validation checks the data again on your server — stronger and more reliable.
- Always validate on the server, even if you use client-side checks.
Example (HTML5):
<input type=”email” name=”email” required placeholder=”Your Email”>
<input type=”password” name=”password” minlength=”8″ required placeholder=”Your Password (at least 8 characters)”>Example (Simplified JavaScript):
const form = document.getElementById(‘myForm’);
const emailInput = document.getElementById(’email’);form.addEventListener(‘submit’, function(event) {
if (!emailInput.value.includes(‘@’)) {
alert(‘Please enter a valid email address.’);
event.preventDefault(); // Stop the form from submitting
}
});
3. Sanitize Inputs
- Remove unnecessary or dangerous characters (like <script> tags or SQL keywords) from user input before using it.
- Sanitization involves cleaning up the user input to remove any potentially harmful code or characters. For example, you might remove HTML tags from a comment field.
- Validation involves checking if the data meets your expected format, length, and type. For example, ensuring an email address has an “@” symbol and a domain, or that a phone number only contains digits.
- Using Server-Side Languages: Languages like PHP, Python, Java, and Node.js offer built-in functions and libraries for robust input validation.
Example (Simplified PHP):
<?php
if ($_SERVER[“REQUEST_METHOD”] == “POST”) {
$email = filter_var($_POST[“email”], FILTER_SANITIZE_EMAIL);
if (!filter_var($email, FILTER_VALIDATE_EMAIL)) {
$emailErr = “Invalid email format”;
}$comment = htmlspecialchars($_POST[“comment”]); // Basic sanitization
// … more validation and processing …
}
?>
4. Limit File Uploads
If your form allows file uploads:
- Set file type and size restrictions
- Rename uploaded files
- Store them outside of the public web directory
- Scan files with antivirus tools
WordPress Website Owners: Secure Your Forms with These Plugins
If you use WordPress, these plugins can help you build safer, validated forms:
- User-friendly drag-and-drop builder
- Built-in spam protection and input validation
- Option to block suspicious IPs
- Strong field-level validation options
- Integrates with reCAPTCHA and Akismet
- Useful for complex or dynamic forms
Sucuri Security Plugin
- Doesn’t build forms, but adds firewall protection and helps detect malicious activity that can come through vulnerable forms.
Magento Users, Don’t Worry — We’ve Got You Too
Use Built-In Validation Classes
Magento 2 has built-in validation methods in the form.js component — use them! For example, setting a field to data-validate=”{required:true}” enforces mandatory input.
Sanitize Server-Side
Always clean input data before storing or displaying it. Magento modules should use built-in PHP sanitization functions like filter_var() or Magento’s own \Magento\Framework\Escaper.
Use Security Extensions
Consider using security extensions from trusted vendors, like:
- Amasty Security Suite
- Mageplaza Security
- Two-Factor Authentication by Magento

Conclusion
Input validation might sound a bit technical, but it’s really about being a responsible doorkeeper for your website. By carefully checking what information you let in through your forms, you can prevent errors, keep your data clean, improve user experience, and, most importantly, protect your website and its visitors from malicious attacks.
For more cybersecurity updates, stay tuned to MalVirus.








