Greenshift Vulnerability Affects 50,000+ WordPress Websites
Imagine your website is like your digital home. You’ve got a front door for visitors and maybe a back door for deliveries. Now, what if someone found a way to sneak through that back door without you knowing? That’s kind of what happened with a popular WordPress plugin called GreenShift.
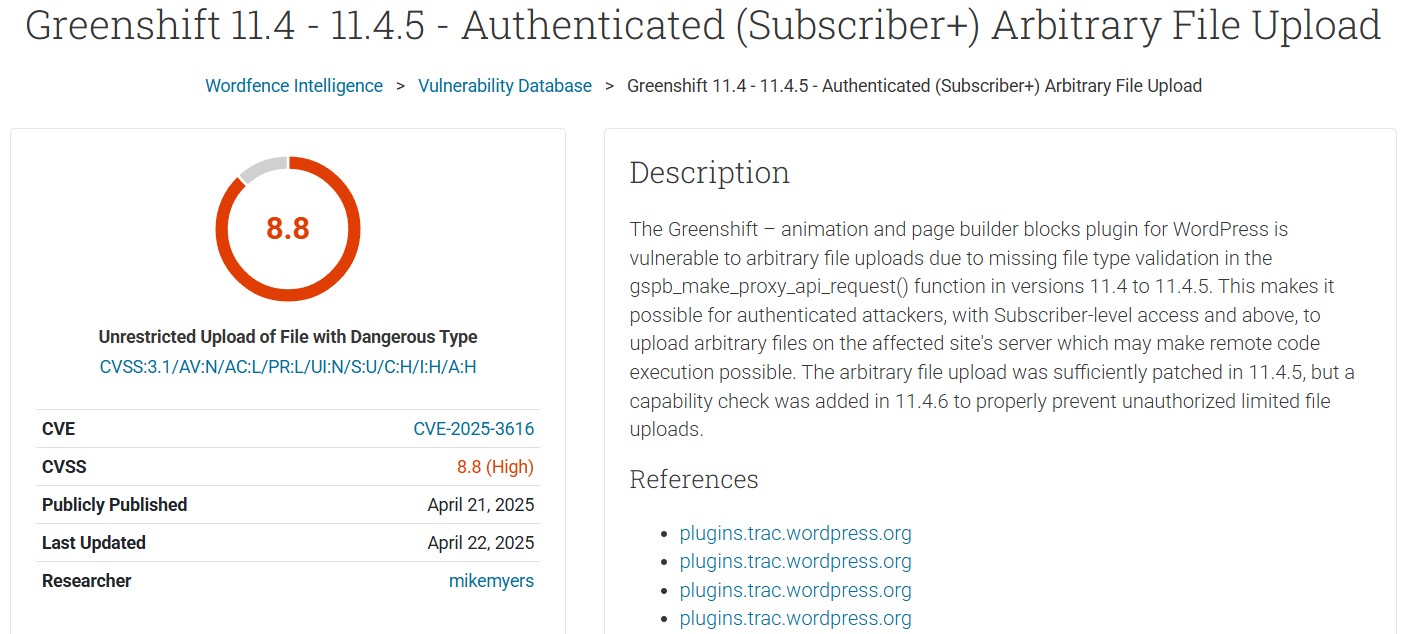
A recent discovery has revealed a critical security flaw in the GreenShift WordPress plugin, which is used by over 50,000 websites. This vulnerability, if exploited, could allow attackers to take full control of affected sites. The issue was first reported by Wordfence, a leading WordPress security company, on April 14, 2025.
What are Greenshift – animation and page builder blocks?
Greenshift is a WordPress plugin that offers animation tools and page builder blocks to help create modern, interactive websites. It’s built on the Gutenberg editor and allows users to design visually rich pages with features like scroll animations, hover effects, dynamic content, and advanced layouts—all without coding.
It’s used to enhance user experience and make websites more engaging through smooth animations and customizable content blocks.
A Hidden Weak Spot
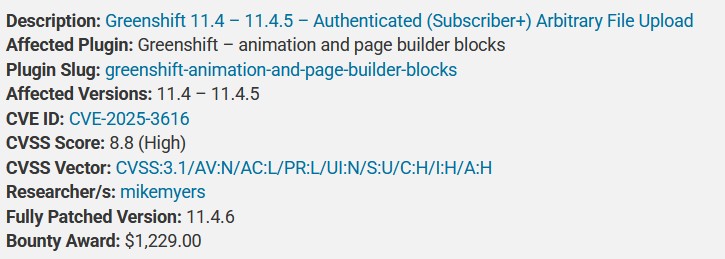
The vulnerability lies in the GreenShift plugin, specifically in versions 11.4 to 11.4.5. It allows attackers with basic access (like subscribers) to upload harmful files to a website. These files can then be used to execute malicious code, potentially leading to a complete site takeover.
It turns out there was a weakness, a sort of unlocked back door, in the GreenShift plugin. This weakness could let bad guys upload any kind of file they wanted onto websites using GreenShift. Think of it like someone being able to drop off a virus or a secret spy program right into your digital living room!
What is a backdoor?
A backdoor on a website is a hidden way for a hacker to get into the site without needing a password.
Even if you fix the main problem or change your login credentials, the hacker can still sneak in using the backdoor. It’s like a secret key they leave behind so they can come back later.

How Was It Discovered?
A security researcher, known as mikemyers, identified the flaw and reported it through the Wordfence Bug Bounty Program. The vulnerability was introduced on April 10, 2025, and was reported just four days later. Thanks to the quick action of both the researcher and the GreenShift development team, a patch was released on April 15, 2025, followed by another update on April 17, 2025.
Where’s the Vulnerability?
The issue comes from a shortcode in the plugin that allows file uploads. This shortcode uses a function called handle_file_upload() located in this file:
./wp-content/plugins/gsv-blocks/includes/shortcodes.php
The exploit comes from missing file type validation in the gspb_make_proxy_api_request() function. Let’s imagine a simplified (and vulnerable) snippet of PHP code within the GreenShift plugin that might have been responsible for handling file uploads (again, this is a conceptual example and not the actual GreenShift code):
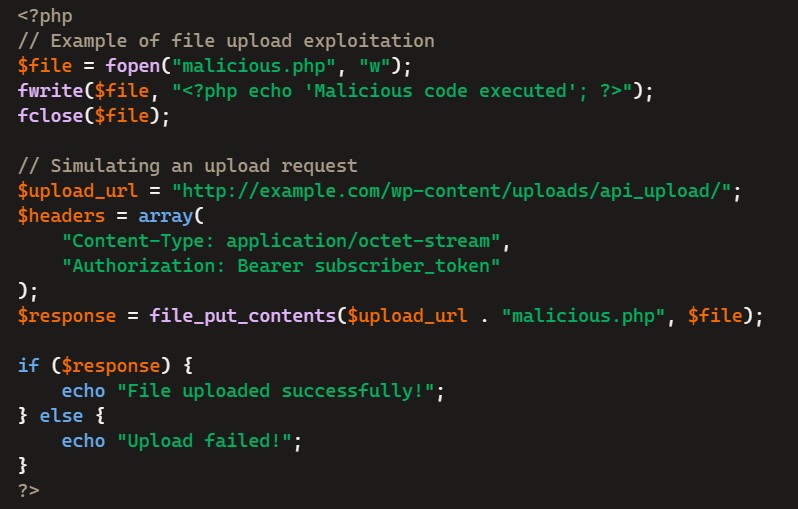
This code demonstrates how an attacker could upload a malicious PHP file to a vulnerable site. Once uploaded, the file could be accessed and executed remotely, leading to a complete site takeover.
Thousands of Websites at Risk
Wordfence estimates that a whopping 50,000 WordPress websites might have this problem. That’s a lot of online homes that could be vulnerable! The vulnerability is connected to a shortcode handler within the plugin that allows file uploads. Unfortunately, this shortcode didn’t check what kind of file was being uploaded. As a result, hackers could upload dangerous files (like a .php backdoor). If these bad guys get their files onto a website, they could do all sorts of nasty things, like:
- Mess up your website: They could change how it looks or even break it completely.
- Steal information: They might try to grab personal details from your visitors or even your own login information.
- Use your website for bad stuff: They could turn your website into a launching pad for other attacks without you even realizing it.
What Should You Do?
If you’re using the GreenShift plugin, it’s crucial to update to the latest version (11.4.6 or higher) immediately. Older versions are vulnerable and could already be compromised. Website administrators should also check their upload directories for suspicious files and monitor user activity.
- Update Immediately – Make sure your plugin is updated to version 6.7.8 or later.
- Scan Your Website – Use a malware scanner (like Sucuri or Wordfence) to check for suspicious uploads.
- Check Your Uploads Directory – Manually review files in /wp-content/uploads/ — look for unusual .php, .txt, or .ico files.
- Harden File Uploads – Restrict executable permissions on your uploads folder, and consider disabling PHP execution there.
- Use a Firewall – A Web Application Firewall (WAF) can block upload attempts and other malicious behavior before it reaches your website.
Wrapping Up!
The GreenShift vulnerability is a reminder that even well-used plugins can open the door to big risks. If you’re running a WordPress site, take this as a nudge to keep your plugins updated and stay alert. A few simple steps can go a long way in keeping your site safe.