Google AdSense Hijack: Malware Campaign Targets WordPress Websites
How to Protect Your WordPress Site from Google AdSense Hijack
Cybercriminals are now hijacking Google AdSense on WordPress websites, injecting unauthorized ads and silently stealing valuable resources from site owners. This alarming campaign was brought to light by Puja Srivastava, a seasoned Security Analyst with over 7 years of hands-on experience in malware detection and website security.
In her recent research about Google AdSense hijack, Puja Srivastava dives into this emerging malware trend, sharing how attackers are embedding fake Google AdSense code into websites, manipulating traffic, and ultimately earning from someone else’s hard work.
What’s Really Happening?
Websites running on WordPress are being targeted by attackers who inject scripts that show unwanted ads. These aren’t your typical ad popups—these are carefully crafted injections that use Google AdSense code to make it look legitimate. However, the earnings go straight to the attacker’s account.
This tactic mirrors an earlier case that Puja Srivastava had explored, where hackers used Google Tag Manager to insert credit card skimming code into Magento-based eCommerce sites. Once again, trusted platforms are being weaponized.
What Are Google Ads and AdSense?
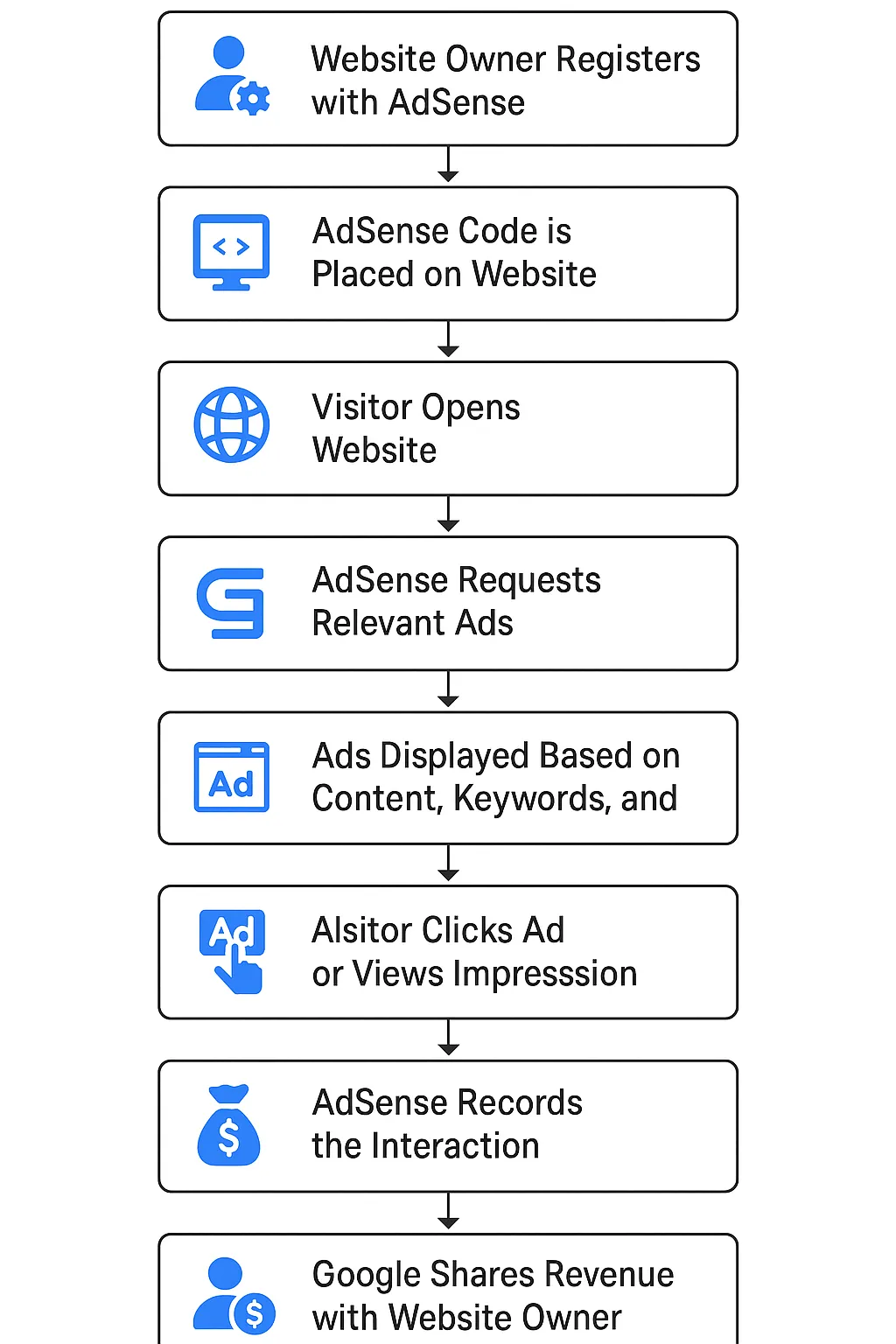
Before diving deeper, let’s clarify what Google Ads and AdSense are:
- Google Ads allows advertisers to pay Google to display their ads across the internet.
- Google AdSense is for website owners to earn money by displaying those ads.
Publishers insert a small JavaScript snippet provided by Google into their websites. In this case, attackers hijack that system for personal gain.
Malicious Ad Code Found – The main culprit of the Google AdSense Hijack
In the affected sites, Puja Srivastava discovered unusual AdSense publisher IDs such as:
pub-9649546719576241pub-7310257338111337
These IDs were linked to suspicious domains like:
link-cpa-anda[.]comasthmanotchcave[.]com
Here’s an example of the injected script, disguised to look like normal AdSense code:
<script async src=”https://pagead2.googlesyndication.com/pagead/js/adsbygoogle.js?client=ca-pub-9649546719576241″ crossorigin=”anonymous”></script>
Puja Srivastava emphasized that this injection isn’t always stored in just one place. Her research found the code embedded in:
functions.phpof active themes- The
mu-pluginsdirectory - Random plugin folders
- The WordPress database (
wp_optionstable)
Persistence Through ads.txt Manipulation
Another alarming discovery was the attackers’ ability to manipulate the ads.txt file. This file tells advertisers who is authorized to sell ad space on a website.
They used PHP code to rewrite and lock in their own AdSense ID, like this:
file_put_contents(‘ads.txt’, ‘google.com, pub-7310257338111337, DIRECT, f08c47fec0942fa0’);
This ensures that even if the infection is cleaned from one location, it can quickly restore itself.
Estimated Reach
At the time of reporting, at least 17 websites were confirmed infected. That number could be much higher, especially since many site owners may not notice the change unless they actively check their code or ad revenue.
Likely Entry Points
While the exact method of infection is still being researched, Puja Srivastava identified a few common weak spots:
- Compromised admin accounts (stolen credentials)
- Vulnerable plugins or outdated themes
- Weak file permissions, allowing code changes from outside
Why Do Hackers Do This?
Simple—money.
By injecting their own Google AdSense hijack code into your site, attackers make money off your traffic. If you’re already using AdSense, they could be redirecting your legitimate revenue to themselves. Some also use this to enable further attacks or malware distribution.
What Can You Do?
If you suspect your site is infected, Puja Srivastava recommends the following steps:
- Scan Your Website
Use tools like Sucuri SiteCheck or VirusTotal to detect malware. - Check for Unusual Code
Look into files likefunctions.php, plugin directories, and database entries for unfamiliar AdSense code. - Review Your ads.txt File
Ensure only your valid publisher ID is listed. - Update Everything
Keep WordPress, plugins, and themes updated. - Change Admin Passwords
And enable two-factor authentication for added security. - Restore from Clean Backup
If possible, roll back to a clean version of your website.
You can also report the compromised Google AdSense account.
The above image depicts how a hijacked Google AdSense account can affect your business. It can simply ruin your day.
Staying vigilant is key. If you’re unsure, seek help from professional website security services. It’s better to act early than let attackers profit from your hard work.
This latest wave of WordPress infections shows how cybercriminals are using legitimate tools—like Google AdSense—for illegal gain. Puja Srivastava’s analysis highlights the importance of regular site maintenance, deep malware scanning, and strong security practices.
Must Read: We posted this article on Fake Google Meet Pages and you bet this is an interesting one!
With attackers constantly evolving, site owners must stay alert. As Puja Srivastava rightly points out in her research, “Trusted platforms are being turned into attack tools. If we don’t monitor our sites, we won’t even notice until it’s too late.”
Did you know? You can protect your server from DDoS attack, here’s how.
Stay safe. Stay updated. Stay Tuned to MalVirus. And don’t let someone else cash in on your hard-earned traffic.