Fake Booking.com Ads Funnel Travellers into an AsyncRAT Trap
AsyncRAT via fake Booking.com domains: What You Must Know
Cybercriminals could use fake booking.com domains to promote ads, game sites, and social media links. A single click could lead users to a CAPTHCA page that claims to be benign but stealthily captures clipboard information, suggesting a twisted PowerShell command be executed. If you heed the suggestion, AsyncRAT—an advanced remote-access Trojan—will be granted access to your PC. This article is based on an original report by Pieter Arntz, a cybersecurity researcher at Malwarebytes.
How the detour works
The lure
- Ads and posts stuffed with travel-keywords steer users to a fake Booking.com domain.
- The destination URL rotates every two-to-three days, making takedown harder.
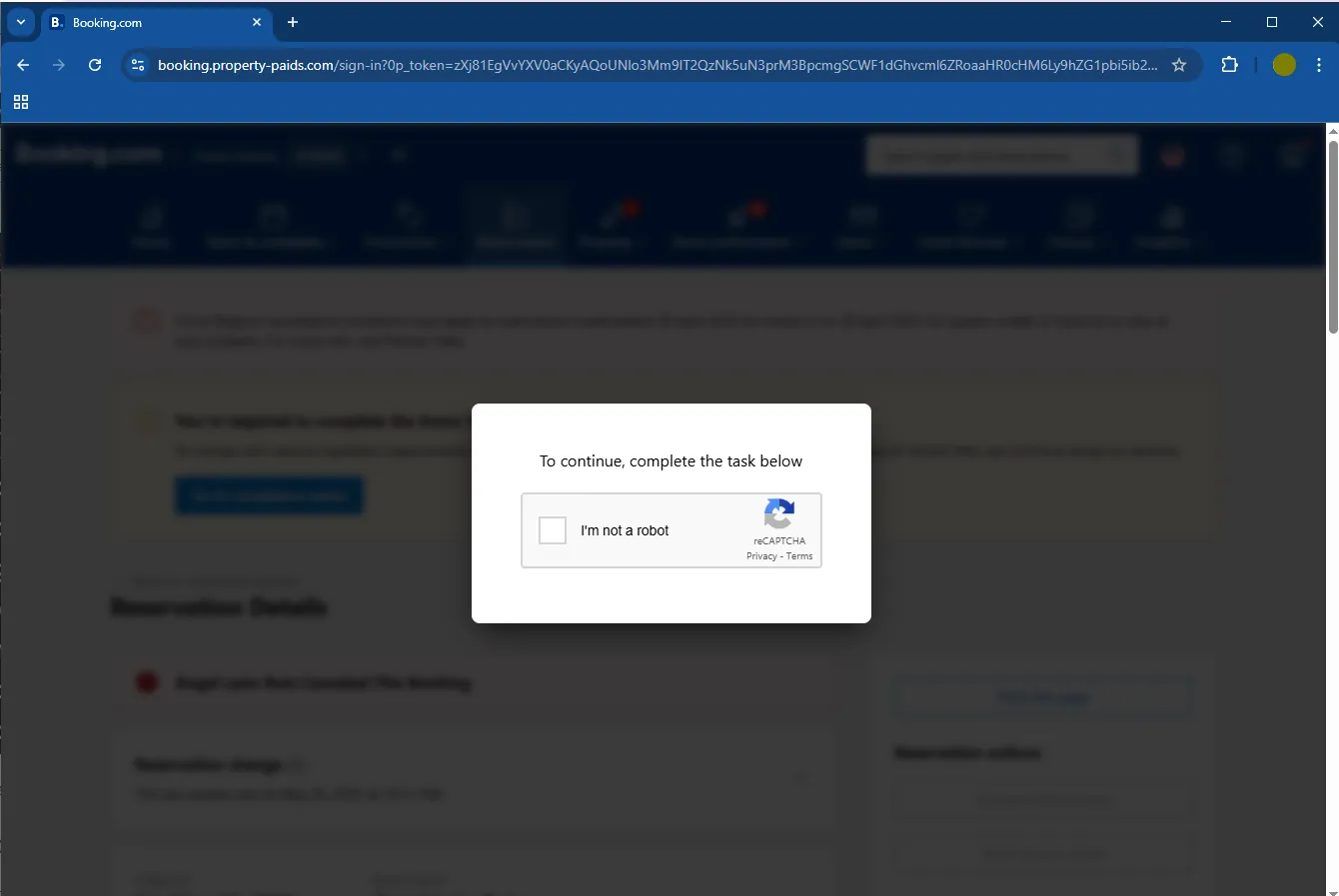
The fake CAPTCHA
- A checkbox pops up; ticking it grants the site permission to write to your clipboard—a red flag on its own.
- Chrome raises a vague warning, while Malwarebytes Browser Guard shouts a clearer alert.
The poisoned clipboard
- Attackers drop an obfuscated PowerShell line—Invoke-RestMethod followed by Invoke-Expression—that fetches ckjg.exe and then Stub.exe from bkngnet[.]com (and similarly named domains).
The payoff: AsyncRAT
- Stub.exe is flagged as Backdoor AsyncRAT, giving crooks remote control for data theft, credential scraping, and potential identity hijacking.
Pieter Arntz uncovers
Malwarebytes’ threat analyst, Pieter Arntz, is famed for his meticulous examination of clipboard hijacking and PowerShell exploitation. Arntz first spotted the campaign in mid-May and in his research, Arntz scanned through an ever-changing list of lookalike domains and noted that 40% of travelers initiate a general search, creating a major target for phishers.
How to stay safe
- Avoid clicking sponsored links right now.
- Disregard all instructions claiming to copy and execute commands. Command Prompt will never be executed from a window asking to paste commands.
- Use layered security measures. Extensions to browsers, such as Malwarebytes Browser Guard, can stop clipboard manipulations.
- PowerShell should be disabled unless used; in that case, set to tight execution policies.
- Teach through video demonstrations of the scam so they understand its implications, especially non-technical colleagues.
Indicators of Compromise (IOCs)
Some of the domains which have been found in the redirect chain are listed below. The sub-domain usually has a “booking.” prefix to enhance its credibility:
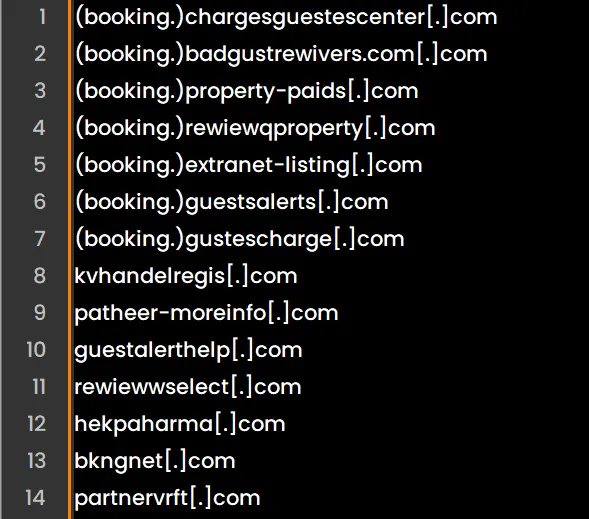
As can be seen, these addresses are often updated, so blocking by pattern (\\\”booking.\\\” + random-looking domain) is more efficient than intricate blacklists.
How to protect yourself online
- Watch where you click. Sponsored links can be scams.
- CAPTCHAs do not ask for clipboard automation.
- Use multiple layers of protection. Browser plugins such as Malwarebytes Browser Guard can use copy and paste protection to stop click horse before damages are done.
- PowerShell lockdown. If you choose not to use it, limit access and disable; otherwise set execution policies to be very strict.
- Train your staff. A short demonstration showing non-technical coworkers the convincing nature of the scam helps them realize the threat.
For more real-world cyber threat breakdowns, scam alerts, and expert tips to stay secure online, keep visiting Malvirus.com—your trusted hub for cybersecurity insights.