Fake Google Meet Page: Trick Users into Downloading Malware
Cybercriminals are getting incredibly clever. They’re now using fake Google Meet pages to trick people into downloading dangerous software. This isn’t just a simple trick; it’s a multi-layered trap designed to bypass your usual defenses and plant nasty PowerShell malware deep inside your computer.
A recent alarm bell, highlighted by Puja Srivastava from Sucuri, details a particularly sneaky campaign: a fake Google Meet page designed to trick users into running potent PowerShell malware. This isn’t just a simple trick; it’s a multi-layered trap built to bypass your usual defenses and plant nasty software deep inside your computer.
Must Read: Google AdSense Hijack – A Recent Malware Campaign
How the Attack Works
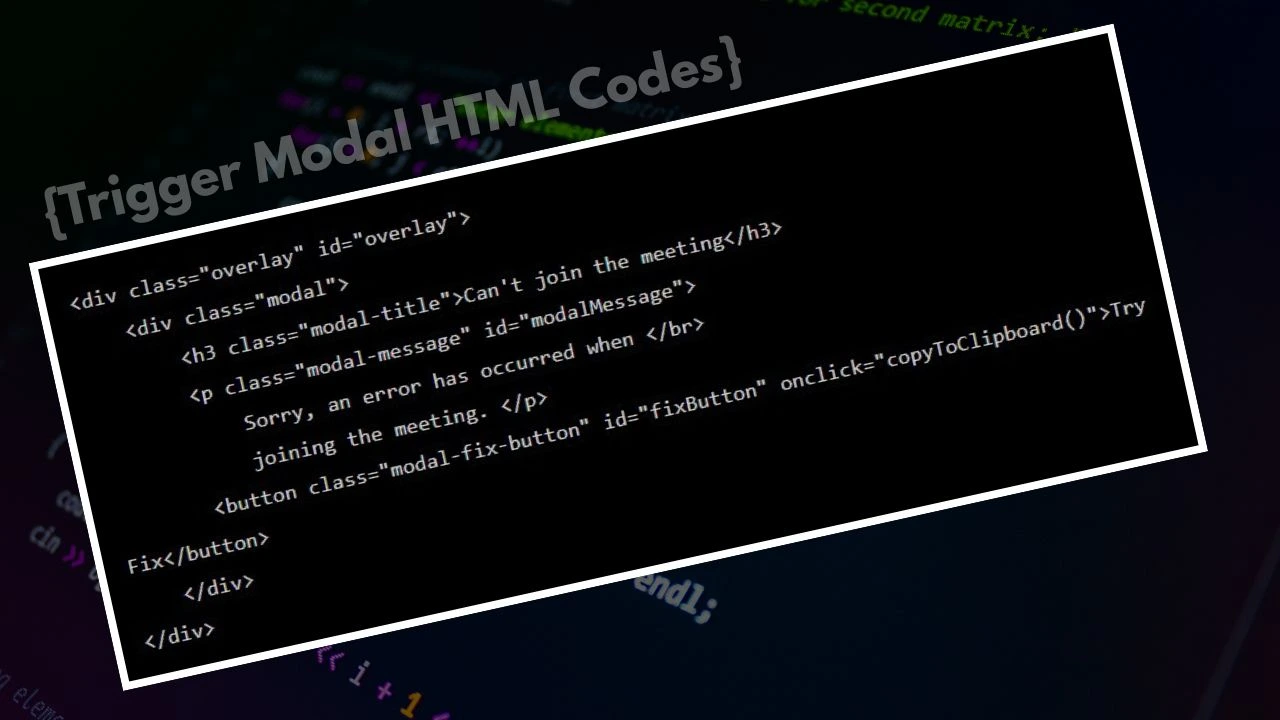
The malicious campaign begins when potential victims receive links to what appears to be a legitimate Google Meet session. However, instead of connecting to an actual meeting, users are redirected to a carefully crafted fake page that mimics Google Meet’s interface.
The Sneaky Setup: A Meeting That Isn’t
The fraudulent page displays a message claiming that users need to download and run a PowerShell script to “enable microphone and camera access” for the meeting. This social engineering tactic exploits users’ familiarity with software requiring permissions for hardware access, making the request seem reasonable.
The Tricky Download: Malware in Disguise
Puja Srivastava, a security researcher at Sucuri who analyzed the campaign, explained that the fake pages are designed with remarkable attention to detail. “The attackers have created convincing replicas that include Google’s branding, color schemes, and typical user interface elements that users expect to see,” Puja noted in the Sucuri’s blog post.
PowerShell Script
The malicious PowerShell scripts are hosted on compromised websites, adding another layer of legitimacy to the attack. When users download and execute these scripts, they unknowingly download and install malware on their systems that can perform various malicious activities.
Upon following the instructions, users inadvertently execute a PowerShell script that downloads and runs a Remote Access Trojan (RAT). This malware grants attackers unauthorized access to the victim’s system, potentially leading to data theft, surveillance, or further exploitation.
The Malicious Payload: XR.txt
When users follow the prompt, they execute a PowerShell command that downloads and runs a Remote Access Trojan (RAT). The command fetches a file named XR.txt, which contains an obfuscated PowerShell script designed to decode itself at runtime and execute malicious code directly in memory.
“The script begins by displaying a “Verification complete!” message box to the user, a tactic to reassure the victim that their action was successful and legitimate, while the malicious operations continue in the background.” said Puja.
The core functionality is hidden within a heavily obfuscated PowerShell command that dynamically decodes and executes a further malicious payload. This payload includes downloading and executing a batch file named noanti-vm.bat.
The noanti-vm.bat RAT Malware
The noanti-vm.bat file is a heavily obfuscated Windows batch script detected as a Trojan or RAT on VirusTotal. It employs tactics common in evasive malware, such as string slicing and environment variable manipulation, to construct real commands letter by letter from scattered, innocent-looking values.
This technique allows the attacker to execute commands that enable delayed variable expansion in the batch environment, facilitating further dynamic command building and execution of malicious activities, explains Puja.
Impact of the Malware
The PowerShell malware deployed in this campaign exhibits several concerning capabilities. Once executed, the script establishes persistence on the infected system and can download additional malicious payloads from remote servers.
Security researchers found that the malware includes functionality for:
- Data Exfiltration: The script can collect sensitive information from infected systems, including browser data, stored passwords, and system information
- Remote Access: Attackers can establish backdoor access to compromised systems for future use
- Credential Harvesting: The malware specifically targets stored authentication credentials from various applications
- System Reconnaissance: The script gathers detailed information about the infected system’s configuration and installed software
The use of PowerShell as the delivery mechanism is particularly concerning because it’s a legitimate Windows administration tool that’s present on most Windows systems by default. This allows the malware to execute without triggering security alerts that might be raised by unknown executable files.
In a separate campaign that Puja Srivastava analyzed last month, cybercriminals were found injecting malicious Google AdSense code into compromised WordPress websites. This “ad-jacking” technique allows attackers to monetize compromised websites by replacing legitimate advertisements with their own, generating revenue while potentially exposing visitors to additional malicious content.
The AdSense hijacking campaign, Puja Srivastava’s research article, demonstrates how attackers are increasingly focusing on monetization strategies that can generate ongoing revenue from compromised systems, rather than simple one-time data theft operations.
Detection and Prevention
Identifying these fake Google Meet pages requires careful attention to several indicators:
- URL Verification: Legitimate Google Meet sessions use URLs that begin with “meet.google.com” or “hangouts.google.com.” Any deviations from these official domains should raise immediate suspicion.
- Permission Requests: Google Meet never requires users to download and execute PowerShell scripts for basic functionality like microphone and camera access. Such requests are clear indicators of malicious intent.
- Browser Permissions: Legitimate video conferencing applications request hardware permissions through standard browser interfaces, not through downloaded scripts.
- SSL Certificate Validation: Users should verify that meeting pages display valid SSL certificates issued to Google, rather than generic or suspicious certificates.
Conclusion and Future Outlook
These incidents underscore the evolving nature of cyber threats, where adversaries employ increasingly sophisticated methods to deceive users and exploit trusted platforms. By mimicking familiar interfaces and leveraging social engineering tactics, attackers can bypass traditional security measures. Continuous vigilance, user education, and robust security practices are essential to counteract such threats.
These incidents highlight how even tech-savvy users can fall victim to cleverly disguised attacks. Staying informed about the latest threats, stay connected to MalVirus and adopting a proactive security mindset is no longer optional, it’s essential.