Sophisticated PHP Malware Leverages ZIP Archives for WordPress Redirects
Sneaky PHP Malware Uses ZIP Archive to Redirect WordPress Visitors
Last month a WordPress site began exhibiting unexplained redirects. Sucuri security analyst Puja Srivastava investigated and discovered a sophisticated PHP malware deeply hidden in the site’s core files.
This was not a simple redirect hack but a complex attack aimed at search-engine poisoning and unauthorized content injection. In her analysis, Srivastava explains that the malware hijacks site authority to boost spammy pages in search results, making detection and cleanup very difficult.
Initial Findings
On inspection, Srivastava found two suspicious lines added to wp-settings.php (a core WordPress file). The first line extracts the bare domain from the host header (stripping “www.” for consistency).
The second line uses PHP’s zip:// stream wrapper to include a PHP file from inside a win.zip archive, keyed by the domain name. In other words, it runs a file named after the site’s domain inside win.zip, which is hidden inside a ZIP file.
This stealthy trick hides the malware code inside what looks like an innocuous archive. When the investigators unpacked win.zip, they found it contained a single, highly obfuscated PHP script – the core of the malware.
Attack Vector & Indicators of Compromise
The key indicators of compromise (IoCs) identified by Sucuri are:
- Malicious include in wp-settings.php: A
zip://win.zip#<hostname>line was injected intowp-settings.php. - Hidden domain-specific payload: Inside
win.zipsits a PHP file named for the host, containing the obfuscated malware code. - Visitor-specific redirect logic: The malware’s payload contains logic to send different content or redirects based on who is visiting (e.g. hiding behavior from bots).
Together, these components show how the attackers embedded the hack deeply in the site and tailored it per-host and per-visitor.
Malware Analysis
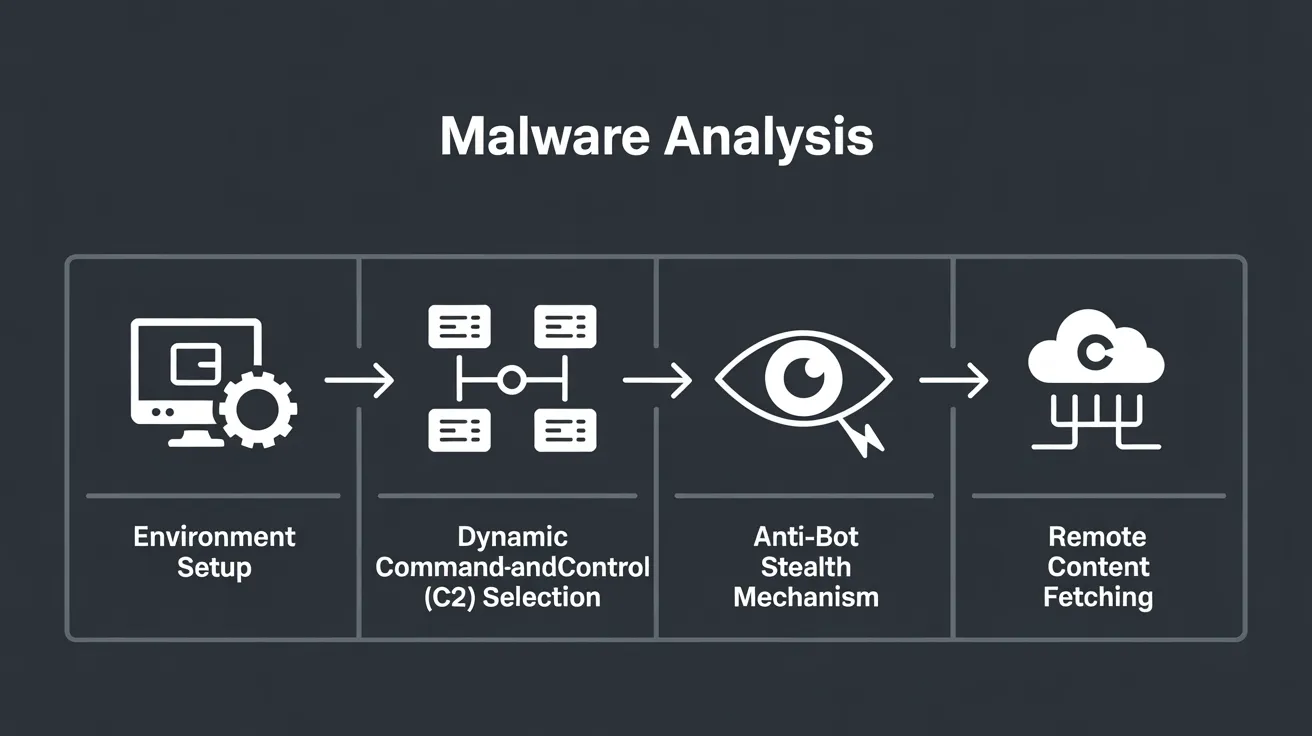
Environment Setup
Once deployed, the malware first configures its environment. It suppresses errors and detects the current protocol (HTTP vs HTTPS). Checking HTTPS allows it to load resources without triggering mixed-content warnings. In short, it ensures it can run silently and fetch external code safely.
Dynamic Command-and-Control (C2) Selection
A clever feature is dynamic C2 server selection. The malware chooses which remote server to contact based on the requested URL. This means different parts of the site may use different attacker-controlled domains, making takedown harder. (A “C2” server is simply a system the attacker uses to control the malware and receive stolen data.) By rotating through C2 servers, the attack stays resilient and difficult to block.
Anti-Bot Stealth Mechanism
To avoid detection, the code checks for known bots and crawlers. If it sees a bot (e.g. Googlebot, Bingbot, Yahoo), it disables its malicious behavior. In practice, this means it won’t redirect or inject spam for search engine crawlers. By staying dormant during bot visits, the infection stays hidden in search results and evades automated scanners. This stealth tactic makes the hack very hard for site owners to notice through normal means.
Remote Content Fetching
The payload also reaches out to the attacker’s server to fetch further instructions or content. It contacts a URL (like an attacker-hosted contents.php) and can send back site information via POST. This lets the attacker update the malicious code or track the status of the infection in real time.
Website File Manipulation (SEO Poisoning)
A main goal is to poison search results. The malware intercepts requests for Google verification files (e.g. google*.html) and responds with attacker-controlled content to fool Google Search Console into thinking the attacker owns the site.
It also manipulates robots.txt and sitemap directives: it fetches a robots.txt base (or starts with “Allow: all”) and then appends a <sitemap> line pointing to a spammy sitemap URL on the attacker’s server. This forces search engines to crawl the attacker’s malicious pages on the victim’s domain, boosting their search rankings at the expense of the legitimate site.
Dynamic Redirection
Finally, the malware dynamically serves redirects to visitors. For example, Sucuri found the hacked site redirected specific paths to different spam domains:
products.php→wditemqy.enturbioaj[.]xyzdetail.php→oqmetrix.icercanokt[.]xyz- All other pages →
yzsurfar.icercanokt[.]xyz
These three attacker-controlled domains (and others) are used to serve malicious content. By targeting different URL paths, the attackers could run parallel SEO campaigns or serve different spam pages to different audiences.
Impact of the Malware
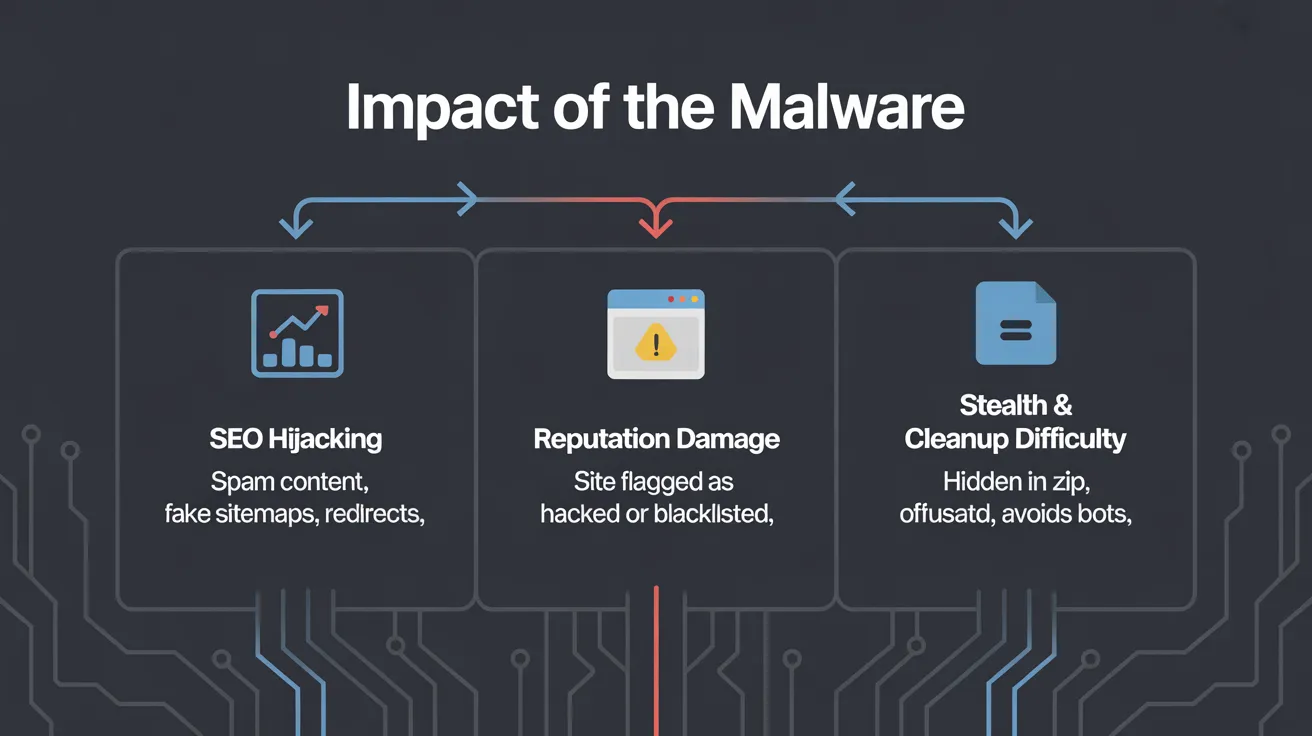
Sucuri notes several harmful effects of this infection:
- SEO Hijacking: The attackers inject spammy content, fake sitemaps, and 301 redirects to make search engines elevate the attacker’s malicious pages using the victim site’s authority.
- Reputation Damage: Infected sites risk being flagged as unsafe by browsers, security scanners, and Google. This can earn the site “This site may be hacked” warnings or blacklisting.
- Stealth and Cleanup Difficulty: Because the malware hides in a ZIP include, uses heavy obfuscation, and avoids bots, it is very hard to detect. Ordinary scan tools may miss it and cleanup often requires expert help.
Prevention and Mitigation
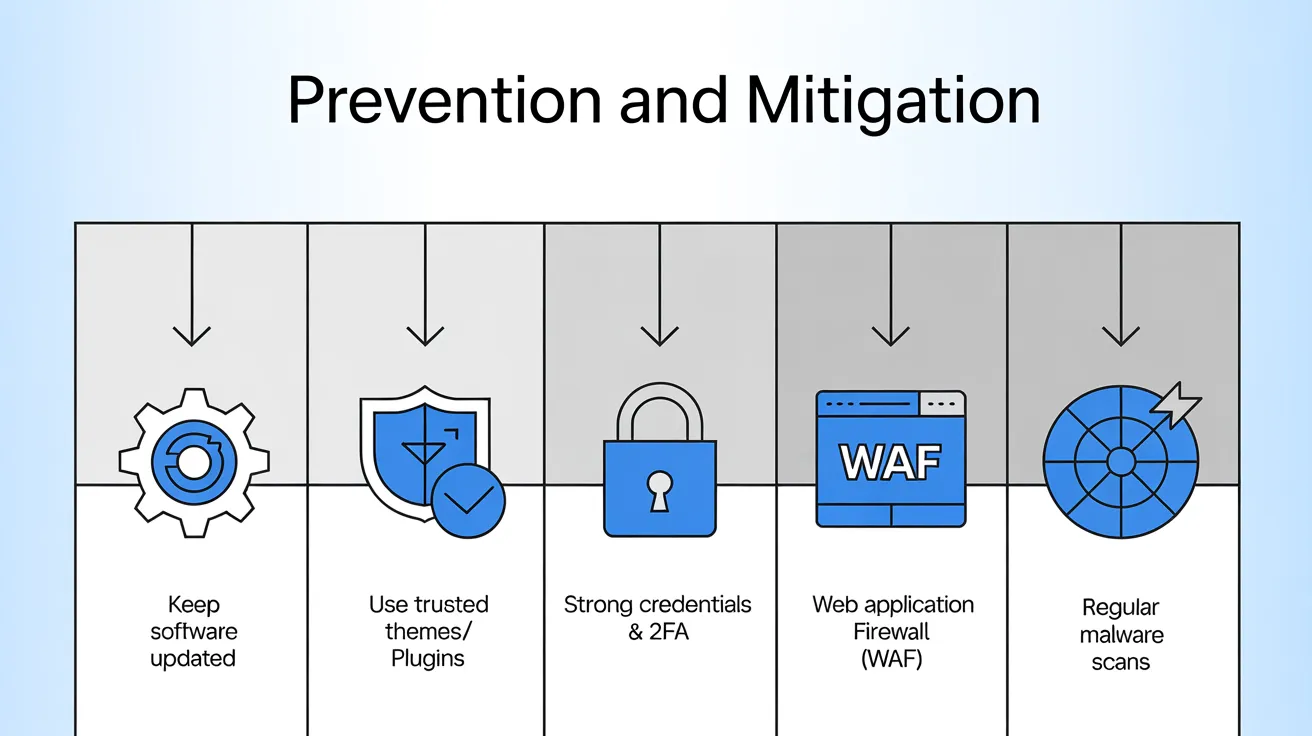
To defend against such threats, Sucuri recommends standard best practices:
- Keep software up to date: Always use the latest WordPress core, themes, and plugins. Many attacks exploit known vulnerabilities in outdated code.
- Use trusted themes/plugins: Install extensions only from the official WordPress repository or well-known developers. Avoid pirated or unvetted add-ons, which often carry malware.
- Strong credentials & 2FA: Use unique, complex passwords for all site accounts (admin, FTP, database). Enable Two-Factor Authentication (2FA) for admin logins. This makes unauthorized access much harder.
- Web Application Firewall (WAF): Deploy a WAF (like Sucuri’s) to block malicious traffic before it reaches your site. A good firewall can stop exploit attempts or strange file includes.
- Regular malware scans: Set up automated, frequent scans of your site for malware. Early detection helps you clean infections before they spread.
Important Notes:
- The use of PHP’s
zip://wrapper means the malware is hidden inside a ZIP archive, not in a normal PHP file. Standard file-scanning tools might not look inside ZIPs, so specialized scans or manual code review is often needed. - The anti-bot behavior means the hack often never appears in Google’s cached pages or normal browsing. Site owners may see nothing suspicious in search results. To detect it, manually visit your site in an incognito browser or use a security plugin to reveal hidden redirects.
- Always backup your site before attempting any cleanup. Given the complexity here, consider professional help if you suspect infection. An incomplete cleanup can leave hidden backdoors.
Final words by Puja
Advanced malware campaign indicates some intelligence; for instance, usage of ZIP-based code hiding and bot evasion by the attackers. However, as Srivastava recommends, such vigilance and basic hygiene (and good backups) are the best defense. With these practices, you can greatly reduce the risk of malware hijacking your WordPress site.
Fortunately, site owners can stay a step ahead. Srivastava’s advice: keep software updated, use strong passwords/2FA, employ a firewall, and scan regularly. Such vigilance has been especially emphasized by Puja Srivastava, and basic hygiene (and good backups) are the best defense. With these you can greatly reduce the risk of malware hijacking your WordPress site.