ToolShell Zero-Day: Microsoft Rushes Emergency Patch for SharePoint Exploit
A new and dangerous Microsoft SharePoint Toolshell vulnerability is being actively used by hackers. And Microsoft is racing to stop it.
This urgent warning comes from both the Microsoft Security Blog and a new MSRC advisory published on July 22, 2025.
ToolShell is no ordinary malware. It’s a post-exploitation framework, giving hackers full remote access and stealthy control over infected systems.

What Is a ToolShell and Why Is It Dangerous?
ToolShell uses PowerShell and encrypted payloads to sneak into networks without being seen.
Once in, it helps attackers move quietly, collect data, and stay hidden for long periods.
It also avoids detection by running fileless, meaning there’s nothing to easily scan or delete.
Who Is at Risk?
Any organization using Microsoft SharePoint could be a target.
Businesses, schools, and government networks are all potential victims, especially if they haven’t updated yet.
Hackers are actively scanning for vulnerable systems, so time is of the essence.
What’s CVE-2025-53770?
This is a remote code execution (RCE) vulnerability in Microsoft SharePoint Server.
If exploited, it allows attackers to run malicious code remotely without needing a user to click anything.
In short: It’s dangerous, it’s being used now, and it needs fixing ASAP.
What Should You Do Now?
Here are some quick actions to stay safe:
- Update all SharePoint servers right now
- Monitor systems for strange PowerShell activity
- Review logs for unusual access patterns
Also, keep your security tools up to date, antivirus alone won’t catch this.
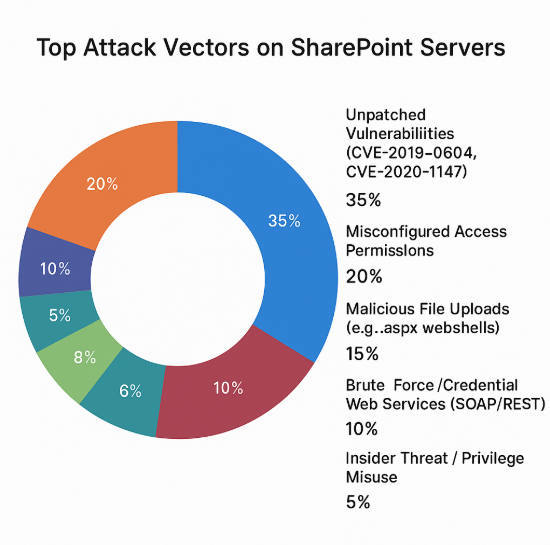
What Makes ToolShell So Dangerous?
ToolShell is tricky. It uses fileless techniques and encrypted PowerShell scripts.
This lets it stay under the radar of traditional security tools.
According to Microsoft, attackers used it after gaining access through a SharePoint vulnerability that hadn’t been patched.
Microsoft’s Emergency Response
Microsoft moved fast. They’ve released out-of-band security updates for supported SharePoint versions.
This patch closes the vulnerability and blocks ongoing attacks using CVE-2025-53770.
They also worked with global partners to disrupt the attackers and limit further damage.
You can find official update links and details in the full MSRC customer guidance.
It’s Tips and Tricks time!
- Enable Automatic Updates – If your systems support it, turn on automatic updates for Microsoft products. It reduces the risk of falling behind on critical patches.
- Use Microsoft Defender for Endpoint – Defender for Endpoint can detect and alert you about ToolShell activity and suspicious PowerShell use.
- Keep an Eye on PowerShell Logs – ToolShell loves PowerShell. Make sure logging is turned on and watch for strange scripts or execution patterns.
Before you leave this page…
This news is a strong reminder that zero-days don’t wait, and neither should you.
At MalVirus, we’re committed to helping you stay ahead in cybersecurity. Stay safe. Stay updated. And patch fast.