Step-by-Step Guide to Detect DNS Spoofing
Ever typed a website name into your computer, like your favorite social media site, and ended up exactly where you expected? That’s thanks to a helpful system like a super-fast phonebook for the internet. But what if someone could secretly change the numbers in that phonebook?
What if, when you asked for your social media site’s address, you were given the address of a fake website instead? That sneaky trick is called DNS spoofing. It’s like someone playing a prank on your computer, leading it to the wrong online door without you knowing.
DNS spoofing is a serious cyber threat. It involves changing DNS records to send users to fake websites. As we use the internet more, knowing about DNS spoofing is key to spotting and stopping it.
We’ll show you how to find DNS spoofing. This is important in today’s digital world. We aim to give you a full guide on how to keep your online world safe.
By the end of this article, you’ll know how to spot and fight DNS spoofing attacks. This will make your online browsing safer.
Key Points:
- Understanding the basics of DNS spoofing and its implications.
- Learning the importance of detecting DNS spoofing.
- Gaining insights into the detection process.
- Identifying measures to prevent DNS spoofing attacks.
- Enhancing your cybersecurity knowledge to protect your online presence.
Understanding DNS Spoofing: The Fundamentals
The Domain Name System (DNS) is at the Internet’s core. It’s vital but can be attacked, like DNS spoofing. Think of DNS as a phonebook, turning domain names into IP addresses for computer communication.
What is DNS, and how does it work?
DNS is a system that translates domain names into IP addresses. When you enter a URL, a DNS query is sent. This query goes through various DNS servers to find the IP address.
The process starts with the resolver checking its cache. It then queries root DNS servers and authoritative name servers. Knowing this helps spot vulnerabilities.
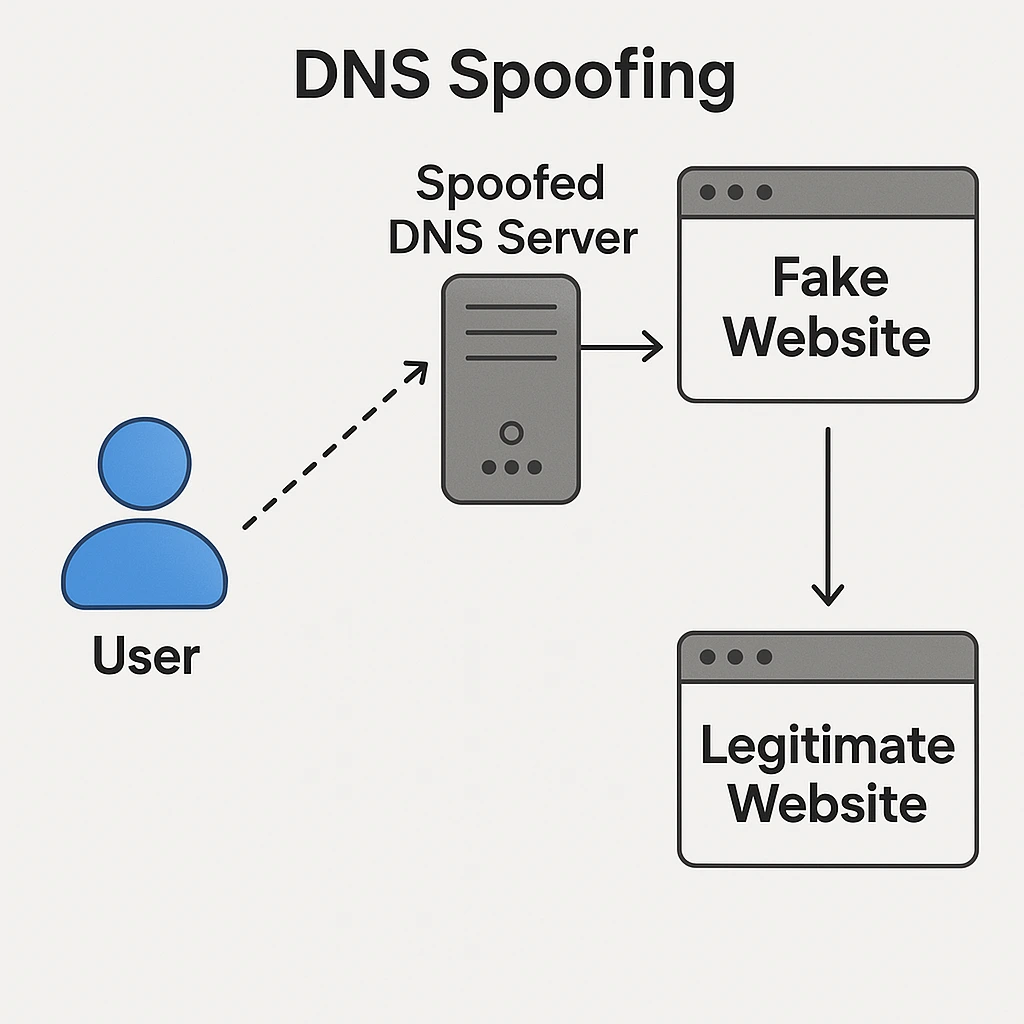
Definition and Mechanics of DNS Spoofing
DNS spoofing, or cache poisoning, happens when an attacker corrupts a resolver’s cache. This redirects users to fake sites. It’s done through malware or DNS protocol vulnerabilities.
An attacker intercepts DNS queries and sends fake responses. If accepted, the resolver caches the false info. This can affect many users.
Common Types of DNS Spoofing Attacks in Networks
Networks face DNS spoofing attacks like MitM and cache poisoning. MitM attacks intercept communication. Cache poisoning corrupts the DNS cache with false info.
| Type of Attack | Description | Impact |
| Man-in-the-Middle (MitM) | Intercepting DNS queries and responses | Data theft, eavesdropping |
| Cache Poisoning | Corrupting DNS cache with false information | Widespread redirection to malicious sites |
The Dangers of DNS Spoofing for Organisations and Individuals
Understanding DNS spoofing is key to keeping our online world safe. It can cause big problems like data theft, financial loss, and harm to our reputation. It’s important for both groups to know these risks and act to protect themselves.
Data Theft and Privacy Concerns
Data theft is a big risk with DNS spoofing. Attackers can trick users into giving out personal info like passwords and bank details. This not only hurts our privacy but also puts company data at risk.
Financial Implications of DNS Attacks
The money side of DNS spoofing attacks is scary. Financial loss comes from theft and the cost of fixing things. For companies, this can be a big financial hit.
Reputation Damage and Regulatory Compliance Issues
DNS spoofing can also hurt a company’s reputation. If customers go to fake sites, they lose trust. In the world, companies must follow data protection laws. Not stopping DNS spoofing attacks can lead to legal trouble.
Signs That You Might Be a Victim of DNS Spoofing
Spotting DNS spoofing needs careful watching and knowing the small signs. It’s key to catch the signs of a DNS spoofing attack in network security.
Unusual Network Behaviour Indicators
One key sign is odd network behaviour. This might show as unexplained changes in network settings or odd data transfer patterns. You might also see frequent disconnections or slow speeds without a clear reason.
Website Redirection and Certificate Warnings
Being sent to strange or suspicious websites is another clue. Browsers might also show certificate warnings when trying to visit secure sites. These warnings mean the connection might not be safe.
Performance Issues and Connectivity Problems
DNS spoofing can also cause performance issues or connectivity problems. You might find some websites or services unavailable or your internet not working right.
Distinguishing DNS Spoofing from Regular Network Issues
It’s vital to tell DNS spoofing from normal network problems. While some signs might look the same, regular and unexplained issues could mean DNS spoofing. Watching your network closely and knowing the signs helps fight DNS spoofing attacks.
DNS Analysis Tools and Their Configuration
DNS analysis tools are vital for fighting DNS spoofing. Tools like DNSQuerySniffer and DNSInspector let us check DNS traffic live. This helps us spot spoofing attempts.
Getting these tools set up right is essential for good detection.
Packet Sniffers and Traffic Analysers
Packet sniffers and traffic analysers, like Wireshark, are must-haves. They let us look closely at DNS traffic. This way, we can spot DNS spoofing signs.
Wireshark Configuration for DNS Monitoring
To use Wireshark for DNS monitoring, we need to set up filters. This captures DNS traffic. Then, we can check the packets for spoofing signs.
Wireshark helps us see if DNS responses are real.
Interpreting Packet Capture Results
Understanding packet capture results needs knowledge of DNS and spoofing methods. By looking at the packets, we can find oddities that might mean DNS spoofing.
These could be things like wrong TTL values or DNS response mismatches.
Using these tools and methods helps us better detect DNS spoofing. It keeps our networks safe. Following DNS spoofing detection best practices and using strong DNS spoofing countermeasures are key to network security.
Step-by-Step Guide to Detect DNS Spoofing
Detecting DNS spoofing needs a careful approach. First, we must understand DNS basics and its weaknesses. A detailed guide is key to spotting and stopping DNS spoofing attacks.
Preliminary Network Assessment
The first step is a detailed network check. We look at the network setup, find weak spots, and learn how DNS works. Network admins must make sure DNS servers and clients are set up correctly to avoid attacks.
Configuring Your Detection Tools
To find DNS spoofing, we need the right tools. We pick network monitoring and DNS analysis tools to spot odd DNS traffic. Wireshark and DNSQuerySniffer are great for this. Setting these tools up right is key for good detection.
Analysing DNS Query Responses
Checking DNS query answers is very important. We look at the answers from DNS servers for any oddities. Good DNS answers should match the domain’s expected IP addresses. If they don’t, it might be a spoofing attack.
Verifying DNS Cache Integrity
Checking the DNS cache is also essential. We look for any odd entries in the cache.
Command-Line Tools for Cache Inspection
Tools like ipconfig /displaydns on Windows or sudo rndc dumpdb -cache on Linux help check the cache. They show us what’s in the cache, helping spot bad entries.
Identifying Suspicious Cache Entries
We find odd cache entries by looking for strange domain names or IP addresses.
“A thorough check of DNS cache entries is vital for spotting DNS spoofing attacks,”
cybersecurity experts say. Keeping an eye on DNS cache entries helps catch attacks early.
By following this guide, network admins can find DNS spoofing and stop it.
Advanced Techniques for DNS Spoofing Detection
As DNS spoofing gets more complex, we need to update our detection methods. We must use advanced techniques to spot and block DNS spoofing attempts.
DNS Response Validation Methods
Validating DNS responses is key to detecting spoofing. We check if DNS responses are genuine. DNSSEC helps by digitally signing DNS data, making it hard for attackers to alter responses undetected.
TTL Value Analysis and Anomaly Detection
Looking at TTL (Time To Live) values is also important. TTL shows how long a DNS record is valid. If TTL values change suddenly, it might mean an attack. We should watch these values closely for any odd changes.
| TTL Value Range | Normal Behaviour | Potential Spoofing Indicator |
| 0-100 | Common for frequently updated records | Sudden changes or inconsistencies |
| 100-86400 | Typical for standard DNS records | Unusual patterns or unexplained changes |
| >86400 | Often used for less frequently updated records | Significant deviations from expected values |
Cross-Referencing DNS Responses with Authoritative Servers
Checking DNS responses against authoritative servers is a strong method. We compare the DNS responses from local servers with those from the real name servers.
Setting Up Automated Comparison Systems
To make this easier, we can use automated systems. These systems compare DNS responses all the time. They need tools that can check both local and authoritative servers and then compare the results.
Interpreting Discrepancies in DNS Records
If we find differences in DNS records, it could mean spoofing. We need to look into these differences to find out why and act on it.
Using these advanced methods helps us better detect DNS spoofing. This protects our networks and users from threats.
Troubleshooting Common Issues During DNS Spoofing Detection
When we tackle DNS spoofing detection, we face several hurdles. These include dealing with false positives, fixing tool setup issues, and handling confirmed attacks. It’s a complex task that requires careful attention.
Dealing with False Positives
False positives can really slow us down. To overcome this, we need to tweak our detection tools. Keeping them updated and trained on new patterns helps lower false positives.
Resolving Tool Configuration Problems
Setting up tools correctly is key to detecting DNS spoofing. If tools are misconfigured, we get the wrong results. It’s vital to follow the manufacturer’s setup guidelines.
Escalation Procedures for Confirmed Attacks
When we confirm a DNS spoofing attack, we need a solid plan. This includes isolating systems, telling others, and working with authorities.
| Incident Response Activities | Description | Responsible Team |
| Detection | Identifying DNS spoofing attacks using monitoring tools | Security Operations |
| Containment | Isolating affected systems to prevent further damage | Incident Response Team |
| Eradication | Removing the root cause of the DNS spoofing attack | Security Engineering |
| Recovery | Restoring systems and services to normal operation | IT Operations |
Implementing Preventive Measures Against DNS Spoofing
Stopping DNS spoofing needs a mix of strategies. As we use the internet more, keeping our networks safe is key.
DNSSEC Implementation Guide
DNSSEC (Domain Name System Security Extensions) is a top way to stop DNS spoofing. It signs DNS data to keep it real and safe. First, we make a pair of keys: a Zone Signing Key (ZSK) and a Key Signing Key (KSK).
Then, we sign our DNS zone with the ZSK. We publish the public ZSK and the signed zone data.
DNS over HTTPS (DoH) and DNS over TLS (DoT)
Using DNS over HTTPS (DoH) and DNS over TLS (DoT) is also key. These encrypt DNS queries, making them hard to tamper with. DoH uses HTTPS, and DoT uses TLS. Either one boosts our DNS security a lot.
Regular DNS Server Auditing Practices
Checking our DNS servers often is critical. We watch DNS server setups, update software, and look for odd logs. This helps us spot and fix security issues fast.
Employee Training for DNS Security Awareness
Teaching our team about DNS security is vital. We teach them about DNS spoofing risks, how to spot attacks, and the need to follow security rules. A security-aware team can stop many DNS attacks.
With these steps, we can greatly improve our defence against DNS spoofing. This keeps our networks safe from threats.
Final words
We’ve explored how to spot and stop DNS spoofing attacks. By using our guide, you can make your online security much stronger.
It’s important to use the best ways to find and stop DNS spoofing. Our guide shows you the tools and steps to keep your online world safe.
As cyber threats grow, it’s essential to stay alert and act fast. Keep your security up to date and follow the best practices. This will protect your digital world from DNS spoofing and other dangers.








