Email Spoofing Prevention: Best Practices & Security Tips for 2026
Introduction
In today’s world of computers and internet, email has become the foundation of professional communication. Emails are faster, more convenient, and far more efficient than traditional postal letters. But with this ease comes a darker side.
Have you ever come across an email that looks just like it was sent by an official body or someone you know, like your boss but it wasn’t? That’s a classic case of email spoofing. In today’s article, we are going to throw some light on Email Spoofing Prevention methods.
Cyberattackers use this tactic to forge the sender’s identity, making their message appear legitimate. But why? – To trick you into clicking malicious links, sharing confidential data, or even wiring money. It’s a digital impersonation game, the one that hides dangerous intent behind a familiar name.

Here’s the deal…
Email is like the postal service of the internet. We use it for everything – chatting with friends, work stuff, banking, online shopping, you name it. But just like sneaky folks used to forge letters in the old days, there are digital trick-people out there who can pretend to be someone they’re not in your inbox. This trick is called email spoofing, and it’s a big deal.
So, how do we fight back in 2026? It’s all about being smart and setting up some digital defenses. Let’s dive into the best practices and security tips to keep those tricky email spoofers at bay!
Top 10 Security Tips to Prevent Email Spoofing
- Always, Always, Always Check the Sender!
- Hover Before You Click (or Tap with Caution!).
- Be Wary of Unexpected Attachments.
- Educate Yourself and Your Team.
- Implement Email Authentication Protocols (SPF, DKIM, DMARC).
- Enable Multi-Factor Authentication (MFA) Everywhere.
- Use a Robust Email Security Solution.
- Use Strong, Unique Passwords.
- Keep Your Software Updated.
- Have an Incident Response Plan.
But Wait, What Are Some Common Email Spoofing Attacks?
Email spoofing isn’t a single trick; it comes in many forms, each designed to deceive you differently. Understanding these types helps you spot them better.
a) Phishing: Email spoofing isn’t a single trick; it comes in many forms, each designed to deceive you differently. Understanding these types helps you spot them better.
Example From The Past: The infamous Google and Facebook “CEO Fraud” (2013-2015) saw a Lithuanian man impersonating an Asian hardware manufacturer. He sent fake invoices to Google and Facebook, convincing them to wire over $100 million before the scam was uncovered. This was a sophisticated example of how email spoofing can lead to massive financial losses.
b) Spear Phishing: This is like phishing, but it’s highly personalized. Instead of casting a wide net, attackers do their homework. They might know your name, your job title, or even details about your company. The email will look like it’s from someone specific you know or trust – perhaps your boss, a colleague, or a known vendor – and will often ask for something specific, like an urgent money transfer or access to a sensitive document. It leverages social engineering to exploit trust.
Example From The Past: In 2020, an Australian hedge fund, Levitas Capital, reportedly lost millions due to a whaling attack (a type of spear phishing targeting high-level executives). The co-founder received an email seemingly from a trusted source with a fake Zoom link, which led to malware and subsequent financial compromise.
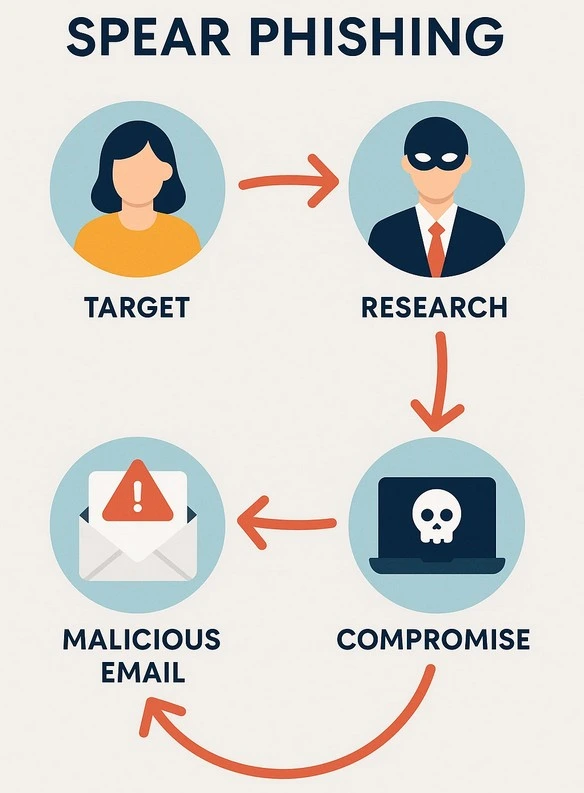
c) Whaling: This is a super-targeted form of spear phishing that goes after the “big fish” – senior executives like CEOs, CFOs, or other high-value targets within an organization. The emails are crafted with extreme care, often mimicking urgent business requests or legal matters, aiming to trick these executives into making large financial transfers or revealing critical company secrets.
Example From The Past: In late 2015, Austrian aerospace company FACC lost approximately $47 million due to a successful whaling attack. An attacker impersonated the CEO and sent an email to an employee in the accounting department, instructing them to transfer a large sum of money for an apparent acquisition project.
d) Business Email Compromise (BEC): This is a broad category where attackers compromise legitimate business email accounts (often through spoofing or phishing) or impersonate executives to trick employees, customers, or partners into transferring funds or sensitive information. It’s often referred to as “CEO fraud” or “invoice fraud.” The key here is tricking employees into performing actions that benefit the attacker, often involving large sums of money.
Example From The Past: The Pepco Group Attack in February 2024 saw the retail conglomerate lose around €15.5 million (about $16.7 million USD) in a phishing attack targeting its Hungarian branch. Attackers leveraged email compromise to redirect payments, showcasing the devastating financial impact of BEC.
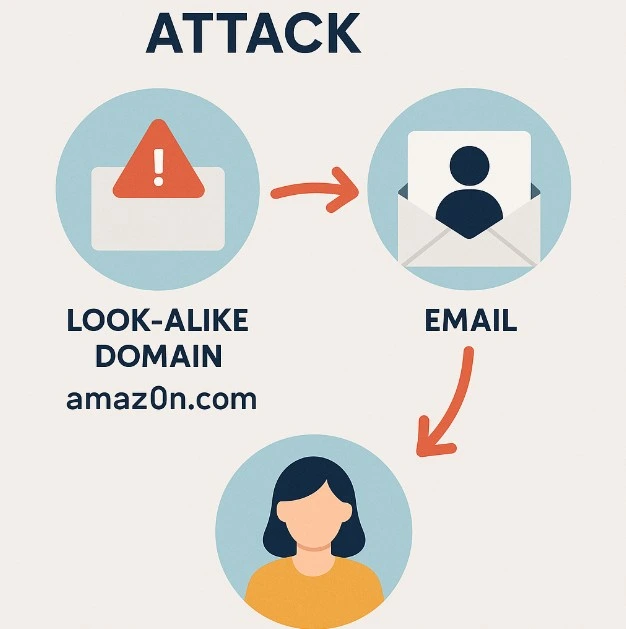
e) Domain Spoofing / Look-alike Domains: This is when attackers register domain names that look incredibly similar to legitimate ones. For example, “amaz0n.com” instead of “amazon.com” (notice the zero instead of the ‘o’). They then use these look-alike domains to send emails that appear legitimate at first glance, hoping recipients won’t notice the subtle difference. This is a common tactic to bypass basic email filters.
Example From The Past: In 2020, attackers used a look-alike domain “micros0ft.com” (with a zero) to impersonate Microsoft and trick users into revealing credentials through phishing emails, successfully bypassing security filters and compromising multiple business accounts.
Security Tips Explained
-
Always, Always, Always Check the Sender!
- How it helps: The “From” name you see in your inbox is easily faked. The actual email address is harder to spoof perfectly.
- Action: When you get an email, especially if it’s unexpected or asks you to do something urgent, don’t just glance at the name. Hover your mouse over the sender’s name (or tap and hold on mobile) to reveal the actual email address. Does support@yourbank.com become bank.support@random-scam.net? That’s a huge red flag! Even if the domain looks similar, like micr0soft.com instead of microsoft.com, be suspicious.
- Here’s how it can look…
——————————————
| Inbox: |
| [From: “Your Bank” <bankupdates@scam.net>] | <— HOVER HERE!
| Subject: Urgent Security Alert |
| |
| Dear Customer, |
| Your account has been locked. Click… |
——————————————
-
Hover Before You Click (or Tap with Caution!).
- How it helps: Malicious links often hide behind innocent-looking text. Attackers use these links to send you to fake websites that steal your information or download malware.
- Action: Before clicking any link in an email, hover your mouse over it. A small pop-up should appear showing the true destination URL. If the text says “Click Here for Banking Login” but the link shows malicious-site.xyz, don’t click it! On mobile, a long press on the link will usually show the URL before you commit.

-
Be Wary of Unexpected Attachments.
- How it helps: Attachments can carry malware, ransomware, or other harmful software.
- Action: If you receive an unexpected attachment, even from someone you know, be extremely cautious. Verify with the sender through a different communication method (like a phone call or a new email thread, not by replying to the suspicious email) before opening it. Look out for unusual file types like .exe, .zip (unless you were expecting a zipped file), or even .js files.
-
Educate Yourself and Your Team.
- How it helps: Humans are often the weakest link in security. Attackers know this and heavily rely on social engineering. Awareness training helps you spot the tricks.
- Action: Regularly refresh your knowledge on phishing and spoofing tactics. For businesses, regular security awareness training sessions and simulated phishing exercises are crucial. These drills can show employees what a real attack looks like and how to react without fear.
-
Implement Email Authentication Protocols (SPF, DKIM, DMARC).
- How it helps: These are the unsung heroes working behind the scenes for your email domain. They tell receiving mail servers whether an email claiming to be from your domain is actually legitimate.
- Sender Policy Framework (SPF): Think of SPF as a guest list for your domain’s email. It’s a record you publish in your domain’s DNS (Domain Name System) that lists all the IP addresses (think of them as digital addresses) that are authorized to send email on behalf of your domain. When an email arrives, the receiving server checks if the sender’s IP address is on your SPF list. If it’s not, it’s a red flag!Your Domain’s DNS -> SPF Record: “Only these IPs can send emails from mydomain.com”Incoming Email -> Sending IP (e.g., 1.2.3.4)Receiving Server checks SPF: Is 1.2.3.4 on the approved list for mydomain.com?
- DomainKeys Identified Mail (DKIM): DKIM adds a digital signature to every outgoing email. It’s like sealing a letter with a unique wax stamp that only you can make. Your email server signs the email with a private key, and the receiving server uses a public key (also published in your DNS) to verify that signature. If the signature doesn’t match or the email content was tampered with, DKIM flags it.Sending Server: Signs email with Private KeyEmail travels with Digital SignatureReceiving Server: Uses Public Key (from DNS) to verify signature
- Domain-based Message Authentication, Reporting, and Conformance (DMARC): DMARC acts as the boss, telling receiving mail servers what to do if an email fails SPF or DKIM checks. You can set a policy:
p=none: Just monitor and report (good for starting out).
p=quarantine: Send suspicious emails to the spam/junk folder.
p=reject: Block suspicious emails entirely.DMARC also provides reports, giving you insights into who is sending emails using your domain, helping you identify and block spoofing attempts.
- Action: If you own a domain (for your business or personal use), work with your IT team or email provider to set up and correctly configure SPF, DKIM, and DMARC records in your DNS. This is one of the most effective technical ways to prevent your domain from being spoofed by others.
- How it helps: These are the unsung heroes working behind the scenes for your email domain. They tell receiving mail servers whether an email claiming to be from your domain is actually legitimate.
-
Enable Multi-Factor Authentication (MFA) Everywhere.
- How it helps: Even if a spoofer manages to trick you into giving up your password, MFA adds another layer of security. It requires a second form of verification, like a code sent to your phone or a fingerprint scan.
- Action: Turn on MFA for all your important accounts: email, banking, social media, shopping sites. Microsoft, for example, states that MFA can block over 99.9% of automated account compromise attacks. It’s that powerful!
-
Use a Robust Email Security Solution.
- How it helps: Advanced email security solutions act as a powerful filter between your inbox and the wild internet. They use AI, machine learning, and threat intelligence to detect and block phishing attempts, malware, spam, and spoofed emails before they even reach your inbox.
- Action: For businesses, investing in a top-tier security solution is crucial. For individuals, make sure your email provider (like Gmail, Outlook, etc.) has strong built-in spam and phishing filters, and consider using reputable antivirus software that includes email scanning.
-
Use Strong, Unique Passwords.
- How it helps: This is cybersecurity 101, but it’s still incredibly relevant. Weak or reused passwords make it easy for attackers to break into your accounts once they’ve spoofed an email and tricked you.
- Action: Use a mix of uppercase and lowercase letters, numbers, and symbols. Don’t use easily guessable information like birthdays or pet names. And most importantly, never reuse passwords across different accounts. A password manager can be a huge help here!
-
Keep Your Software Updated.
- How it helps: Software updates often include critical security patches that fix newly discovered vulnerabilities. If you’re running outdated software, you’re leaving known weaknesses open for attackers to exploit.
- Action: Make sure your email client (like Outlook or Thunderbird), web browser (Chrome, Firefox, Edge), operating system (Windows, macOS, Linux), and even your smartphone apps are always up to date. Enable automatic updates whenever possible.
-
Have an Incident Response Plan.
- How it helps: No defense is 100% foolproof. If an email spoofing attack or a related breach does occur, knowing what to do immediately can minimize damage and speed up recovery.
- Action: For businesses, develop a clear plan: who to contact (IT, security team), how to isolate affected systems, how to notify potentially impacted individuals, and steps for recovery. For individuals, know who to report suspicious emails to (e.g., your email provider, your bank), how to change compromised passwords, and how to scan your devices for malware.
Wrapping It Up!
Email spoofing is a persistent threat that preys on trust and human nature. As cyberattackers get more creative, our defenses need to evolve too. By understanding the common attack methods and diligently applying these security best practices, from the simple act of checking a sender’s true email address to the complex setup of DMARC records, we can significantly reduce our vulnerability.
Stay vigilant, stay informed, and let’s make 2025 a year where email spoofers find it a whole lot harder to trick us at MalVirs!








